
The Brazilian threat actors behind an advanced and modular point-of-sale (PoS) malware known as Prilex have reared their head once again with new updates that allow it to block contactless payment... Read more »

Container technology has gained traction among businesses due to the increased efficiency it provides. In this regard, organizations widely use Kubernetes for deploying, scaling, and managing containerized applications. Organizations... Read more »
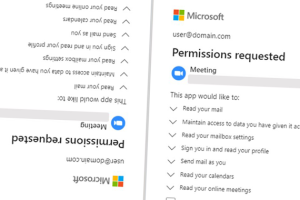
Microsoft on Tuesday said it took steps to disable fake Microsoft Partner Network (MPN) accounts that were used for creating malicious OAuth applications as part of a malicious campaign designed to... Read more »
Two more supply chain security flaws have been disclosed in AMI MegaRAC Baseboard Management Controller (BMC) software, nearly two months after three security vulnerabilities were brought to light in the same... Read more »

Do you know where your secrets are? If not, I can tell you: you are not alone. Hundreds of CISOs, CSOs, and security leaders, whether from small or large... Read more »

A shellcode-based packer dubbed TrickGate has been successfully operating without attracting notice for over six years, while enabling threat actors to deploy a wide range of malware such as TrickBot, Emotet, AZORult, Agent... Read more »
The Russia-affiliated Sandworm used yet another wiper malware strain dubbed NikoWiper as part of an attack that took place in October 2022 targeting an energy sector company in Ukraine. “The NikoWiper... Read more »

Taiwanese company QNAP has released updates to remediate a critical security flaw affecting its network-attached storage (NAS) devices that could lead to arbitrary code injection. Tracked as CVE-2022-27596, the vulnerability... Read more »

GitHub on Monday disclosed that unknown threat actors managed to exfiltrate encrypted code signing certificates pertaining to some versions of GitHub Desktop for Mac and Atom apps. As a... Read more »
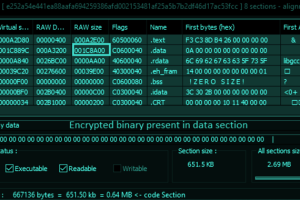
A new Golang-based information stealer malware dubbed Titan Stealer is being advertised by threat actors through their Telegram channel. “The stealer is capable of stealing a variety of information from infected... Read more »

