
Atlassian has released fixes to resolve a critical security flaw in Jira Service Management Server and Data Center that could be abused by an attacker to pass off as... Read more »

F5 has warned of a high-severity flaw impacting BIG-IP appliances that could lead to denial-of-service (DoS) or arbitrary code execution. The issue is rooted in the iControl Simple Object... Read more »

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on February 2 added two security flaws to its Known Exploited Vulnerabilities (KEV) Catalog, citing evidence of active exploitation. The first of the... Read more »
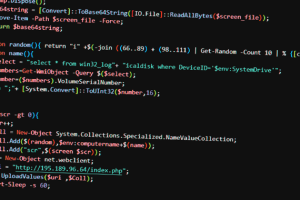
The State Cyber Protection Centre (SCPC) of Ukraine has called out the Russian state-sponsored threat actor known as Gamaredon for its targeted cyber attacks on public authorities and critical information infrastructure... Read more »

A new intelligence gathering campaign linked to the prolific North Korean state-sponsored Lazarus Group leveraged known security flaws in unpatched Zimbra devices to compromise victim systems. That’s according to... Read more »

Over the past few years, cybersecurity has become a major concern for businesses around the globe. With the total cost of cybercrime in 2023 forecasted to reach $8 Trillion... Read more »

At least 1,200 Redis database servers worldwide have been corralled into a botnet using an “elusive and severe threat” dubbed HeadCrab since early September 2021. “This advanced threat actor... Read more »

Cybersecurity researchers have disclosed details of two security flaws in the open source ImageMagick software that could potentially lead to a denial-of-service (DoS) and information disclosure. The two issues, which were... Read more »

A new attack campaign has targeted the gaming and gambling sectors since at least September 2022, just months prior to the ICE London 2023 gaming industry trade fair event that’s scheduled... Read more »

A new exploit has been devised to “unenroll” enterprise- or school-managed Chromebooks from administrative control. Enrolling ChromeOS devices makes it possible to enforce device policies as set by the... Read more »

