
The maintainers of OpenSSH have released OpenSSH 9.2 to address a number of security bugs, including a memory safety vulnerability in the OpenSSH server (sshd). Tracked as CVE-2023-25136, the shortcoming... Read more »
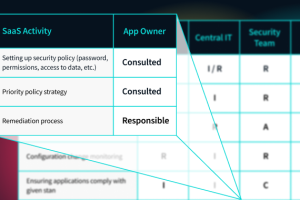
When SaaS applications started growing in popularity, it was unclear who was responsible for securing the data. Today, most security and IT teams understand the shared responsibility model, in... Read more »

An ongoing malvertising campaign is being used to distribute virtualized .NET loaders that are designed to deploy the FormBook information-stealing malware. “The loaders, dubbed MalVirt, use obfuscated virtualization for... Read more »

A new Android banking trojan has set its eyes on Brazilian financial institutions to commit fraud by leveraging the PIX payments platform. Italian cybersecurity company Cleafy, which discovered the... Read more »

VMware ESXi hypervisors are the target of a new wave of attacks designed to deploy ransomware on compromised systems. “These attack campaigns appear to exploit CVE-2021-21974, for which a... Read more »
A zero-day vulnerability affecting Fortra’s GoAnywhere MFT managed file transfer application is being actively exploited in the wild. Details of the flaw were first publicly shared by security reporter Brian Krebs... Read more »
In a continuing sign that threat actors are adapting well to a post-macro world, it has emerged that the use of Microsoft OneNote documents to deliver malware via phishing attacks... Read more »

Two new security weaknesses discovered in several electric vehicle (EV) charging systems could be exploited to remotely shut down charging stations and even expose them to data and energy... Read more »

Cybersecurity is quickly becoming one of the most significant growth drivers for Managed Service Providers (MSPs). That’s the main insight from a recent study from Lumu: in North America, more than... Read more »
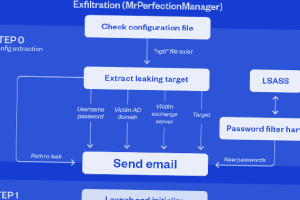
The Iranian nation-state hacking group known as OilRig has continued to target government organizations in the Middle East as part of a cyber espionage campaign that leverages a new backdoor to... Read more »

