
A Russia-linked threat actor has been observed deploying a new information-stealing malware in cyber attacks targeting Ukraine. Dubbed Graphiron by Broadcom-owned Symantec, the malware is the handiwork of an... Read more »

A Russian national on February 7, 2023, pleaded guilty in the U.S. to money laundering charges and for attempting to conceal the source of funds obtained in connection with... Read more »

The Computer Emergency Response Team of Ukraine (CERT-UA) has issued an alert warning of cyber attacks against state authorities in the country that deploy a legitimate remote access software named Remcos.... Read more »
A joint law enforcement operation conducted by Germany, the Netherlands, and Poland has cracked yet another encrypted messaging application named Exclu used by organized crime groups. Eurojust, in a press statement, said the... Read more »

With cyberattacks around the world escalating rapidly, insurance companies are ramping up the requirements to qualify for a cyber insurance policy. Ransomware attacks were up 80% last year, prompting underwriters... Read more »
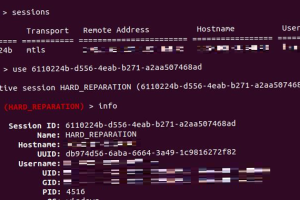
Threat actors are leveraging known flaws in Sunlogin software to deploy the Sliver command-and-control (C2) framework for carrying out post-exploitation activities. The findings come from AhnLab Security Emergency response... Read more »

VMware on Monday said it found no evidence that threat actors are leveraging an unknown security flaw, i.e., a zero-day, in its software as part of an ongoing ransomware attack... Read more »

The first-ever Linux variant of the Clop ransomware has been detected in the wild, but with a faulty encryption algorithm that has made it possible to reverse engineer the... Read more »

An Iranian nation-state group sanctioned by the U.S. government has been attributed to the hack of the French satirical magazine Charlie Hebdo in early January 2023. Microsoft, which disclosed... Read more »

E-commerce industries in South Korea and the U.S. are at the receiving end of an ongoing GuLoader malware campaign, cybersecurity firm Trellix disclosed late last month. The malspam activity... Read more »

