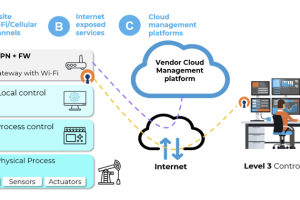
A set of 38 security vulnerabilities has been uncovered in wireless industrial internet of things (IIoT) devices from four different vendors that could pose a significant attack surface for... Read more »

The Hacker News is thrilled to announce the launch of our new educational webinar series, in collaboration with the leading cybersecurity companies in the industry! Get ready to dive... Read more »
A previously unknown threat actor dubbed NewsPenguin has been linked to a phishing campaign targeting Pakistani entities by leveraging the upcoming international maritime expo as a lure. “The attacker sent out... Read more »
The Gootkit malware is prominently going after healthcare and finance organizations in the U.S., U.K., and Australia, according to new findings from Cybereason. The cybersecurity firm said it investigated... Read more »

A single ransomware attack on a New Zealand managed service provider (MSP) disrupted several of its clients’ business operations overnight, most belonging to the healthcare sector. According to the... Read more »

The OpenSSL Project has released fixes to address several security flaws, including a high-severity bug in the open source encryption toolkit that could potentially expose users to malicious attacks.... Read more »

The U.S. National Institute of Standards and Technology (NIST) has announced that a family of authenticated encryption and hashing algorithms known as Ascon will be standardized for lightweight cryptography applications. “The... Read more »

Multiple unpatched security flaws have been disclosed in open source and freemium Document Management System (DMS) offerings from four vendors LogicalDOC, Mayan, ONLYOFFICE, and OpenKM. Cybersecurity firm Rapid7 said... Read more »

A Sydney man has been sentenced to an 18-month Community Correction Order (CCO) and 100 hours of community service for attempting to take advantage of the Optus data breach last year... Read more »

To succeed as a cybersecurity analyst, you need to understand the traits, values, and thought processes of hackers, along with the tools they use to launch their attacks. During... Read more »

