US CISA added actively exploited flaws in Teclib GLPI, Apache Spark, and Zoho ManageEngine ADSelfService Plus to its Known Exploited Vulnerabilities Catalog. US CISA added the following actively exploited... Read more »
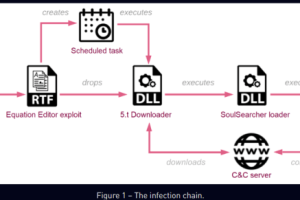
China-linked APT group Sharp Panda targets high-profile government entities in Southeast Asia with the Soul modular framework. CheckPoint researchers observed in late 2022, a campaign attributed to the China-linked... Read more »
Security researchers warn of hacking attempts in the wild exploiting critical vulnerabilities in VMware NSX Manager. Cyber security firm Wallarm is warning of ongoing attacks exploiting the critical flaws,... Read more »
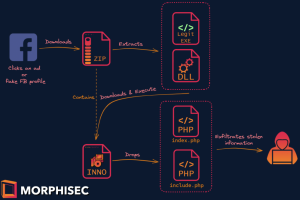
Researchers discovered a new info stealer dubbed SYS01 stealer targeting critical government infrastructure and manufacturing firms. Cybersecurity researchers from Morphisec discovered a new, advanced information stealer, dubbed SYS01 stealer, that since November... Read more »
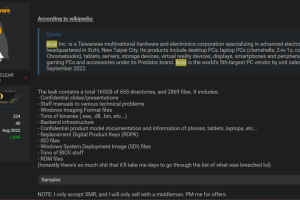
Taiwanese multinational hardware and electronics corporation Acer discloses a data breach after a threat actor claimed the hack of the company. Recently a threat actor announced the availability for sale of... Read more »
Security researcher released a proof-of-concept exploit code for a critical flaw, tracked as CVE-2023-21716, in Microsoft Word. Security researcher Joshua Drake released a proof-of-concept for a critical vulnerability, tracked... Read more »

The LastPass data breach was caused by the failure to update Plex on the home computer of one of the company updates. The security breach suffered by LastPass was... Read more »
Hospital Clinic de Barcelona, one of the main hospitals in the Spanish city, suffered a cyber attack that crippled its computer system. On Sunday, a ransomware attack hit the... Read more »
German police announced to have dismantled an international cybercrime gang behind the DoppelPaymer ransomware operation. Europol has announced that an international operation conducted by law enforcement in Germany and... Read more »
The US government urges cyber security audits of public water systems, highlighting the importance to secure US critical infrastructure. The Biden administration announced on Friday that it will make... Read more »

