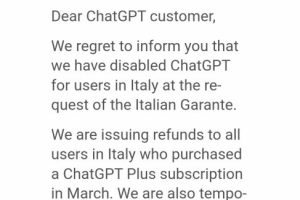
Italy’s data protection agency is temporarily blocking the popular chatbot ChatGPT due to a possible violation of the European data privacy regulation. The Italian Data Protection Authority, Garante Privacy, has temporarily... Read more »
CISA has added nine flaws to its Known Exploited Vulnerabilities catalog, including bugs exploited by commercial spyware on mobile devices. U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added... Read more »
Threat actors are actively exploiting a high-severity flaw in the Elementor Pro WordPress plugin used by more than eleven million websites WordPress security firm PatchStack warns of a high-severity vulnerability in... Read more »

The Cyber Police of Ukraine, with law enforcement officials from Czechia, has arrested several members of a gang responsible for $4.33 million scam. The Cyber Police of Ukraine, with... Read more »
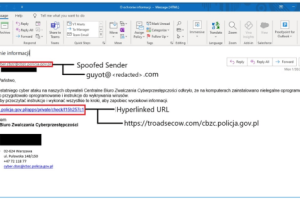
Russian hacking group Winter Vivern has been actively exploiting Zimbra flaws to steal the emails of NATO and diplomats. A Russian hacking group, tracked Winter Vivern (aka TA473), has... Read more »
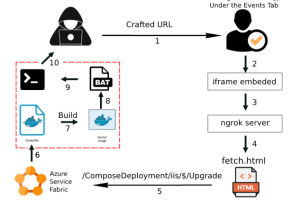
Researchers shared details about a flaw, dubbed Super FabriXss, in Azure Service Fabric Explorer (SFX) that could lead to unauthenticated remote code execution. Researchers from Orca Security shared details... Read more »
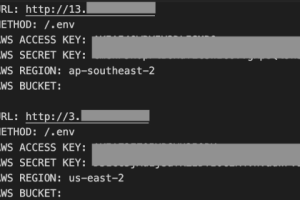
AlienFox is a novel comprehensive toolset for harvesting credentials for multiple cloud service providers, SentinelLabs reported. AlienFox is a new modular toolkit that allows threat actors to harvest credentials... Read more »

Popular voice and video conferencing software 3CX was the victim of a supply chain attack, SentinelOne researchers reported. As of Mar 22, 2023, SentinelOne observed a spike in behavioral... Read more »

Exatrack researchers warn of an unknown China-linked hacking group that has been linked to a new Linux malware, dubbed Mélofée. Cybersecurity researchers from ExaTrack recently discovered a previously undetected malware... Read more »
Taiwanese vendor QNAP warns customers to patch a high-severity Sudo privilege escalation bug affecting NAS devices. Taiwanese vendor QNAP warns customers to update their network-attached storage (NAS) devices to... Read more »

