The development team behind the vm2 JavaScript sandbox library addressed a critical Remote Code Execution vulnerability. The developers behind the vm2 JavaScript sandbox module have addressed a critical vulnerability,... Read more »
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box. CISA adds... Read more »
Andrey Shevlyakov, an Estonian national, was charged in the US with conspiracy and other charges related to acquiring U.S.-made electronics on behalf of the Russian government and military. The... Read more »
US CISA has added Veritas Backup Exec flaws, which were exploited in ransomware attacks, to its Known Exploited Vulnerabilities catalog. U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added... Read more »
Apple released emergency security updates to address two actively exploited zero-day vulnerabilities impacting iPhones, Macs, and iPads. Apple has released emergency security updates to address two actively exploited zero-day... Read more »
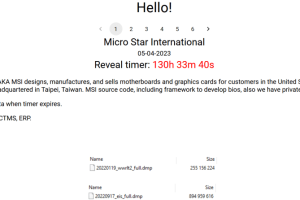
Multinational IT corporation MSI (Micro-Star International) confirms security breach after Money Message ransomware gang claimed the hack. This week the ransomware gang Money Message announced to have hacked the Taiwanese... Read more »
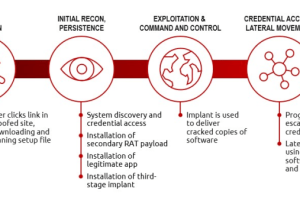
Microsoft announced it has taken legal action to disrupt the illegal use of copies of the post-exploitation tool Cobalt Strike by cybercriminals. Cobalt Strike is a paid penetration testing product... Read more »
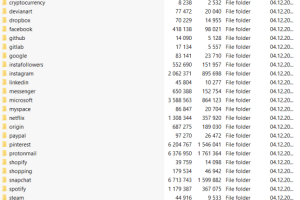
Experts warn that Telegram is becoming a privileged platform for phishers that use it to automate their activities and for providing various services. Kaspersky researchers have published an analysis... Read more »
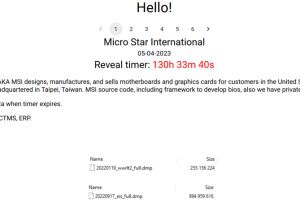
Ransomware gang Money Message claims to have hacked the Taiwanese multinational IT corporation MSI (Micro-Star International). Ransomware gang Money Message announced to have hacked the Taiwanese multinational IT corporation MSI (Micro-Star International).... Read more »
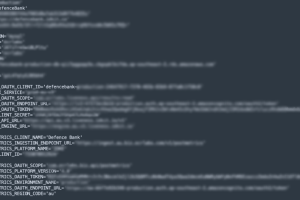
A digital identification tool provided by OCR Labs to major banks and government agencies leaked sensitive credentials, putting clients at severe risk. London-based OCR Labs is a major provider... Read more »

