A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box. Enjoy a new... Read more »

Pro-Ukraine hackers Cyber Anarchy Squad claimed responsibility for the attack that hit Russian telecom provider Infotel JSC. Pro-Ukraine hacking group Cyber.Anarchy.Squad claimed responsibility for an attack on Russian telecom... Read more »

Progress Software released security updates to fix several new SQL injection vulnerabilities in the MOVEit Transfer application. Progress Software has released security updates to address new SQL injection vulnerabilities... Read more »

The University of Manchester suffered a cyberattack, attackers likely stole staff and students’ data from its systems. The University of Manchester, one of the UK’s largest educational institutions, suffered... Read more »
Two Russian nationals have been charged with the hack of the cryptocurrency exchange Mt. Gox in 2011 and money laundering. Russian nationals Alexey Bilyuchenko (43) and Aleksandr Verner (29)... Read more »
This week, the Japanese pharmaceutical giant Eisai has taken its systems offline in response to a ransomware attack. Eisai is a Japanese pharmaceutical company with about 10,000 employees and more than... Read more »
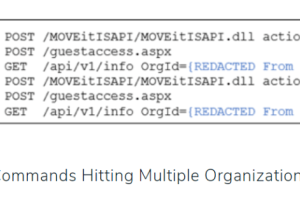
Researchers discovered that the Clop ransomware gang was looking for a zero-day exploit in the MOVEit Transfer since 2021. Kroll security experts discovered that the Clop ransomware gang was... Read more »
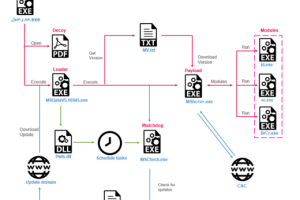
Researchers detected a cyberespionage campaign in Libya that employs a new custom, modular backdoor dubbed Stealth Soldier. Experts at the Check Point Research team uncovered a series of highly-targeted... Read more »
Researchers published an exploit for an actively exploited Microsoft Windows vulnerability tracked as CVE-2023-29336. The Microsoft Windows vulnerability CVE-2023-29336 (CVSS score 7.8) is an elevation of privilege issue that resides in... Read more »

North Korea-linked APT Kimsuky has been linked to a social engineering campaign aimed at experts in North Korean affairs. SentinelLabs researchers uncovered a social engineering campaign by the North Korea-linked APT... Read more »

