Microsoft Patch Tuesday security updates for June 2023 fixed 69 flaws in its products, including six critical issues. Microsoft Patch Tuesday security updates for June 2023 fixed 69 vulnerabilities... Read more »
St. Margaret’s Health in Illinois is partly closing operations at its hospitals due to a 2021 ransomware attack that impacted its payment system. In February 2021a ransomware attack hit... Read more »

A database containing the personal information of more than 8.9 million Zacks Investment Research users was leaked on a cybercrime forum. A database containing personal information of 8,929,503 Zacks... Read more »
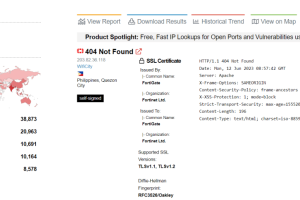
Fortinet addressed a new critical flaw, tracked as CVE-2023-27997, in FortiOS and FortiProxy that is likely exploited in a limited number of attacks. Fortinet has finally published an official advisory about... Read more »

UK communications regulator Ofcom suffered a data breach after a Clop ransomware attack exploiting the MOVEit file transfer zero-day. UK’s communications regulator Ofcom disclosed a data breach after a... Read more »
Security firm Horizon3 released proof-of-concept (PoC) exploit code for the remote code execution (RCE) flaw CVE-2023-34362 in the MOVEit Transfer MFT. MOVEit Transfer is a managed file transfer that... Read more »
Intellihartx is notifying about 490,000 individuals that their personal information was compromised in the GoAnywhere zero-day attack in January. The Clop ransomware group has stolen stole personal and health... Read more »
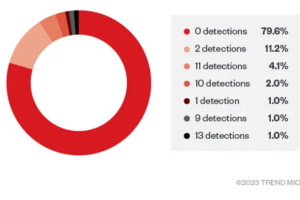
Researchers detailed a fully undetectable (FUD) malware obfuscation engine named BatCloak that is used by threat actors. Researchers from Trend Micro have analyzed the BatCloak, a fully undetectable (FUD) malware obfuscation... Read more »
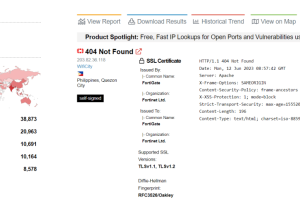
Fortinet released security updates to fix a critical security flaw in its FortiGate firewalls that lead to remote code execution. Fortinet has released security patches to address a critical... Read more »
The Play ransomware attack suffered by the IT services provider Xplain also impacted the national railway company of Switzerland (FSS) and the canton of Aargau. The Play ransomware attack... Read more »

