Swedish software firm Ortivus suffered a cyberattack that has resulted in at least two British ambulance services losing access to electronic patient records. Two British ambulance services were not... Read more »
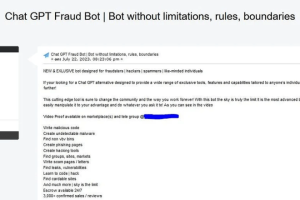
FraudGPT is another cybercrime generative artificial intelligence (AI) tool that is advertised in the hacking underground. Generative AI models are becoming attractive for crooks, Netenrich researchers recently spotted a... Read more »
US CISA added actively exploited Ivanti ‘s Endpoint Manager Mobile (EPMM) vulnerability to its Known Exploited Vulnerabilities catalog. US Cybersecurity and Infrastructure Security Agency (CISA) added actively exploited Ivanti... Read more »
Experts warn of a severe privilege escalation, tracked as CVE-2023-30799, in MikroTik RouterOS that can be exploited to hack vulnerable devices. VulnCheck researchers warn of a critical vulnerability, tracked as... Read more »
Atlassian addressed three vulnerabilities in its Confluence Server, Data Center, and Bamboo Data Center products that can lead to remote code execution. Atlassian has addressed three critical and high severity vulnerabilities impacting... Read more »
VMware fixed an information disclosure flaw in VMware Tanzu Application Service for VMs and Isolation Segment that exposed CF API admin credentials in audit logs. VMware has addressed an... Read more »
Apple released security updates to address an actively exploited zero-day flaw in iOS, iPadOS, macOS, tvOS, watchOS, and Safari. Apple released urgent security updates to address multiple flaws in iOS, iPadOS,... Read more »

Threat actors exploited a zero-day flaw in third-party software in attacks against the ICT platform used by 12 Norwegian ministries. The ICT platform used by twelve ministries of the... Read more »
A new flaw in OpenSSH could be potentially exploited to run arbitrary commands remotely on compromised hosts under specific conditions. Researchers from the Qualys Threat Research Unit (TRU) have... Read more »
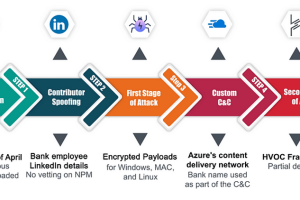
Checkmark researchers have uncovered the first known targeted OSS supply chain attacks against the banking sector. In the first half of 2023, Checkmarx researchers detected multiple open-source software supply chain... Read more »

