Threat actors behind the QakBot malware are still active, since August they are carrying out a phishing campaign delivering Ransom Knight ransomware and Remcos RAT.
In August, the FBI announced that the Qakbot botnet was dismantled as a result of an international law enforcement operation named Operation ‘Duck Hunt.’
Qakbot, also known as QBot, QuackBot and Pinkslipbot, is an info-stealing malware that has been active since 2008. The malware spreads via malspam campaigns, it inserts replies in active email threads.
The Duck Hunt operation involved law enforcement agencies from the U.S., France, Germany, the Netherlands, Romania, Latvia, and the United Kingdom.
Duck Hunt is one of the largest U.S.-led disruptions of a botnet infrastructure used by crooks to commit criminal activities, including ransomware attacks.
Despite the law enforcement operation, the threat actors behind QakBot are still active, Cisco Talos warns.
According to the researchers, the threat actors behind the Qakbot bot have been conducting a campaign since early August 2023. The attacks aimed at distributing Ransom Knight ransomware and the Remcos RAT.
This campaign began before the FBI shut down the Qakbot infrastructure in late August, but it is still ongoing. The experts speculate that the feds’ operation may not have impacted Qakbot spam delivery infrastructure and its impact was limited to part of the C2 infrastructure.
Talos linked this campaign to Qakbot affiliates and speculated that developers are still operational.
The experts tracked this new campaign by connecting the metadata in the LNK files used in the attacks to the machines employed in previous Qakbot campaigns.
“Talos identified new LNK files in August 2023 that were created on the same machine referenced above, but observed that the payload of the files pointed to a network share in the command line that served a variant of Ransom Knight ransomware.” reads the analysis published by Talos.
Some of the filenames observed by Talos are written in Italian, which suggests the campaign is targeting users in Italy. The messages use Zip archives containing the LNK files and an XLL file (XLL is the extension used for Excel add-ins).
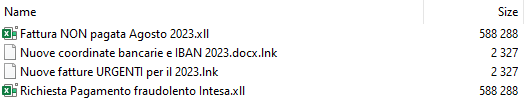
The XLL files are the Remcos backdoor used by the attackers along with Ransom Knight to gain access to the machine after the infection.
“We do not believe the Qakbot threat actors are behind the ransomware-as-a-service offer, but are simply customers of the service. As this new operation has been ongoing since the beginning of August 2023 and has not stopped after the takedown, we believe the FBI operation didn’t affect Qakbot’s phishing email delivery infrastructure but only its command and control servers.” concludes the report. “Though we have not seen the threat actors distributing Qakbot post-infrastructure takedown, we assess the malware will likely continue to pose a significant threat moving forward. Given the operators remain active, they may choose to rebuild Qakbot infrastructure to fully resume their pre-takedown activity.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Malware)
The post QakBot threat actors are still operational after the August takedown appeared first on Security Affairs.

