A new campaign targets Redis servers, this time the malware employed in the attacks is a new variant of the SkidMap malware.
Skidmap is a piece of crypto-miner detected by Trend Micro in September 2019 while it was targeting Linux machines. The malicious code used kernel-mode rootkits to evade detection, it differs from similar miners because of the way it loads malicious kernel modules.
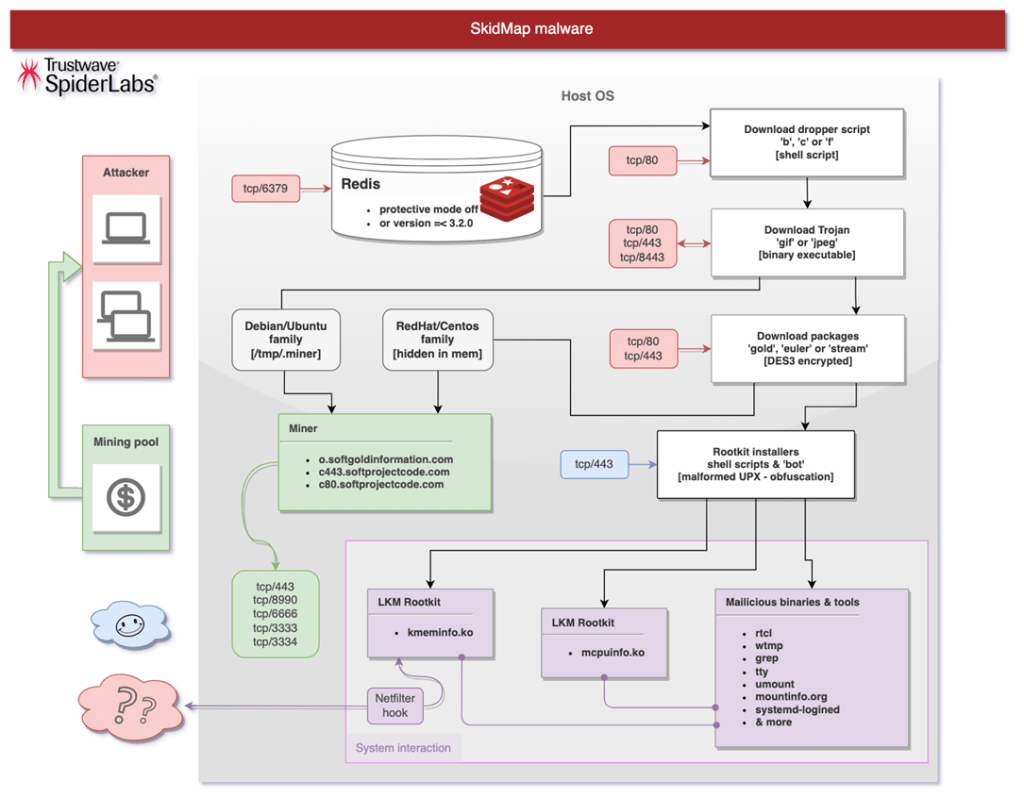
Trustwave researchers spotted a new, improved, and dangerous Skidmap variant, which was designed to target a wide range of Linux distributions, including Alibaba, Anolis, openEuler, EulerOS, Steam, CentOS, RedHat, and Rock.
The variant analyzed by the researchers was observed targeting only open Redis instances (so-called ‘NO AUTH’). No brute-force attacks were observed by the researchers.
“Accordingly, we will distinguish between the two main Linux variants that influenced the infection flow. The first variant is Debian/Ubuntu, the second is RedHat/CentOS.” reads the report published by Trustwave. “The malicious nature of this malware is to adapt to the system on which it is executed. The most important thing for us was to reach down, reveal and describe crucial elements of the rogue application, and thus cut off – we hope – a large part of the earnings from this criminal activity.”
The attack chain starts with an attempt to login to the unsecured Redis instance and set up variables containing base64-encoded cron tasks.
The Cron runs a job every 10 minutes by alternating between ‘curl’ and ‘wget’ to download and execute the dropper script.
Trustwave observed threat actors deploying a dropper shell script that’s designed to distribute the binary executable file (ELF) that masquerades as a GIF image file (while a previous version of the malware used ‘jpeg’).
Once the shell script is deployed, the malware adds ssh keys in standard locations: ‘/root/.ssh/authoried_keys’ and ‘/root/.ssh/authoried_keys2’.
Then the malicious code disables the SELinux and creates a reverse shell that will call back to the C2 every hour via TCP/8443 port.
Depending on the specific Linux distribution and kernel, the malware downloads an appropriate package (named gold, stream, or euler).
The package uses several shell scripts to install the kernel modules, including one to purge the logs and launch a bot that allows operators to retrieve additional rootkit payloads. The mcpuinfo.ko payload is used to hide the miner, while kmeminfo.ko allows the malicious code to inspect network packets and manipulate them. Some variants observed by the experts included a built-in miner.
“The level of advancement of this malware is really high, and detecting it, especially in larger server infrastructures, can be very hard. When testing it on home computers, the only serious indicator that something was wrong was the excessive operation of fans, and in the case of laptops, the temperature of the case” concludes the report that also includes Indicators of Compromise (IoCs). “And finally, what about Redis? Exploiting this flaw doesn’t look complex. And it’s true. Redis is vulnerable by design, and its place is not at the edge of the network. It was designed for a closed environment, and security features were added in later releases.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, malware)
The post A new sophisticated SkidMap variant targets unsecured Redis servers appeared first on Security Affairs.