The AVRecon botnet relies on compromised small office/home office (SOHO) routers since at least May 2021.
In early July, researchers from Lumen Black Lotus Labs discovered the AVRecon botnet that targets small office/home office (SOHO) routers and infected over 70,000 devices from 20 countries.
Threat actors behind the campaign aimed at building a botnet to use for a range of criminal activities from password spraying to digital advertising fraud.
The AVrecon malware was written in C to ensure portability and designed to target ARM-embedded devices. The experts discovered that the malicious code had been compiled for different architectures.
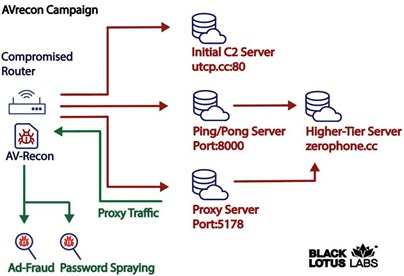
On infected a router, the malware enumerates the victim’s SOHO router and sends that information back to a C2 server whose address is embedded in the code. Then, the infected system starts to begin interacting with a separate set of servers, the so-called second-stage C2 servers.
Black Lotus Labs states AVrecon is one of the largest botnets targeting small-office/home-office (SOHO) -routers seen in recent history. The researchers identified 41,000 nodes communicating with second-stage C2s within a 28-day window.
“Based on information associated with their x.509 certificates, we assess that some of these second stage C2s have been active since at least October 2021. We took a 28-day snapshot of the second stage servers and found more than 70,000 distinct IP addresses communicating with them.” continues the report. “We then investigated how many machines were persistently infected – meaning they communicated with one of the second stage servers for two or more days within the 28-day window – and we identified 41,000 nodes.”
Upon deploying the AVrecon RAT, the malware checks to see if other instances of the malware are already running on the system, it gathers host-based information, and builds the parameters of the C2 channel.
The malware also checks if other instances of itself already running on the host by searching for existing processes on port 48102 and opening a listener on that port.
Most of the infected routers are in the U.K. and the U.S., followed by Argentina, Nigeria, Brazil, Italy, Bangladesh, Vietnam, India, Russia, and South Africa, among others.
The threat actors were observed using the infected machines to click on various Facebook and Google ads, and to interact with Microsoft Outlook. The first activity is part of an advertising fraud effort, and the second activity is likely linked to password spraying attacks and/or data exfiltration.
The popular investigator Brian Krebs and Spur.us investigated the botnet and discovered that the bot is the malware engine behind a 12-year-old service called SocksEscort. Operators behind SocksEscort offer for rent access to compromised residential and small business devices.
“SocksEscort[.]com, is what’s known as a “SOCKS Proxy” service. The SOCKS (or SOCKS5) protocol allows Internet users to channel their Web traffic through a proxy server, which then passes the information on to the intended destination. From a website’s perspective, the traffic of the proxy network customer appears to originate from a rented/malware-infected PC tied to a residential ISP customer, not from the proxy service customer.” reads the post published by KrebsOnSecurity. “Spur tracks SocksEscort as a malware-based proxy offering, which means the machines doing the proxying of traffic for SocksEscort customers have been infected with malicious software that turns them into a traffic relay. Usually, these users have no idea their systems are compromised.”
Customers of the SocksEscort proxy service have to install a Windows-based application to access a pool of more than 10,000 hacked devices worldwide.
Spur researchers created a fingerprint to identify the call-back infrastructure for SocksEscort proxies, they were able to determine that operators use AVrecon to server proxies to the SocksEscort service.
“When Lumen released their report and IOCs [indicators of compromise], we queried our system for which proxy service call-back infrastructure overlapped with their IOCs,” said Spur co-founder Riley Kilmer. “The second stage C2s they identified were the same as the IPs we labeled for SocksEscort.”
KrebsOnSecurity linked the malware proxy network to a Moldovan company named Server Management LLC that also offers VPN software on the Apple Store and elsewhere.
Follow me on Twitter: @securityaffairs Facebook and Mastodon
(SecurityAffairs – hacking, AVRecon)
The post Experts link AVRecon bot to the malware proxy service SocksEscort appeared first on Security Affairs.