Threat actors are actively exploiting a critical flaw, tracked as CVE-2023-28121, in the WooCommerce Payments WordPress plugin.
Threat actors are actively exploiting a recently disclosed critical vulnerability, tracked as CVE-2023-28121 (CVSS score: 9.8), in the WooCommerce Payments WordPress plugin.
The flaw is an authentication bypass issue that can be exploited by an unauthenticated attacker to impersonate arbitrary users, including an administrator, potentially leading to the site takeover.
The popular plugin is installed on over 600,000, the issue impacts versions 4.8.0 through 5.6.1 of WooCommerce Payments.
“Large-scale attacks against the vulnerability, assigned CVE-2023-28121, began on Thursday, July 14, 2023 and continued over the weekend, peaking at 1.3 million attacks against 157,000 sites on Saturday, July 16, 2023.” reads the post published by Wordfence. “The exploit allows unauthenticated attackers to obtain administrative privileges on vulnerable websites, rating it a Critical CVSS score of 9.8.”
WooCommerce addressed the vulnerability in March 2023, while Wordfence announced it has introduced a mitigation for this issue since April 22, 2023.
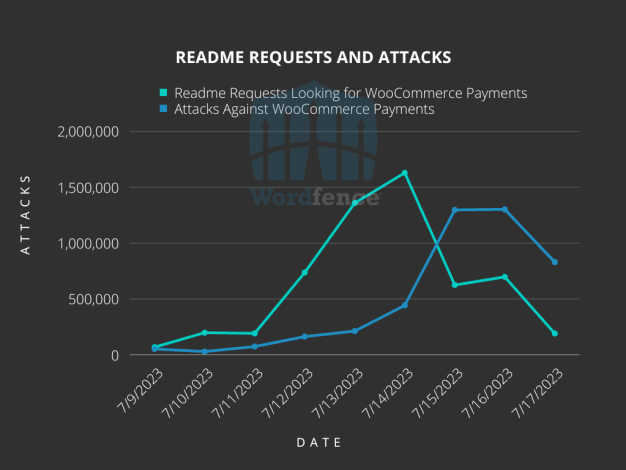
The researchers pointed out that this campaign is targeting a smaller set of websites. Wordfence began seeing early warning signs several days before the main wave of attacks, threat actors were spotted conducting plugin enumeration requests searching for a readme.txt file in the wp-content/plugins/woocommerce-payments/ directory of millions of sites.
The vast majority of actual attacks come from a pool of seven IP addresses, while the readme.txt requests were distributed over thousands of IP addresses. The researchers noticed that nearly 5,000 IP addresses sent both readme.txt requests and actual attacks.
“Common to all exploits targeting the WooCommerce Payments vulnerability is the following header which causes vulnerable sites to treat any additional payloads as coming from an administrative user:
X-Wcpay-Platform-Checkout-User: 1
Many of the requests we’ve seen using this appear to be attempting to use their new administrative privileges to install the WP Console plugin, which can be used by an administrator to execute code on a site” continues the post.
On attackers impersonated administrative with relative privileges sent requests to install the WP Console plugin, which can be used by an administrator to execute code on a site
“These attacks demonstrate significantly more sophistication than similar attacks we’ve seen in the past, including reconnaissance ahead of the main wave of attacks and multiple methods of maintaining persistence using functionality available to administrator-level users.” concludes the report.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, WooCommerce Payments)
The post Hacking campaign targets sites using WordPress WooCommerce Payments Plugin appeared first on Security Affairs.