Avast released a free decryptor for the Akira ransomware that can allow victims to recover their data without paying the ransom.
Cybersecurity firm Avast released a free decryptor for the Akira ransomware that can allow victims to recover their data without paying the ransom.
The Akira ransomware has been active since March 2023, the threat actors behind the malware claim to have already hacked multiple organizations in multiple industries, including education, finance, and real estate,
Akira is a Windows ransomware with a 64-bit Windows binary, it is written in C++ and uses the Boost library to implement the asynchronous encryption code. The authors used Microsoft Linker version 14.35.
In June 2023, the malware analyst rivitna published a sample of the ransomware that is compiled for Linux. This Linux version is 64-bit and also uses the Boost library, it uses the Crypto++ library instead of Windows CryptoAPI.
“During the run, the ransomware generates a symmetric encryption key using CryptGenRandom(), which is the random number generator implemented by Windows CryptoAPI. Files are encrypted by Chacha 2008 (D. J. Bernstein’s implementation).” reads the report published by Avast.
“The symmetric key is encrypted by the RSA-4096 cipher and appended to the end of the encrypted file. Public key is hardcoded in the ransomware binary and differs per sample.”
The ransomware appends .akira extension to the encrypted files and drops a ransom note named akira_readme.txt in each folder.
The researchers discovered a few similarities between the Akira ransomware and the Conti v2 ransomware, a circumstance that suggests the authors may have used the leaked source code of the Conti ransomware.
The list of similarities includes:
- List of file type exclusions.
- List of directory exclusions.
- The structure of the Akira file tail is equal to the file tail appended by Conti.
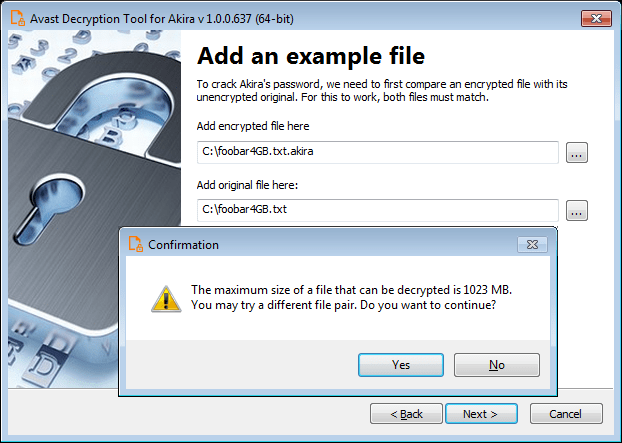
The first step is to download the decryptor binary. Avast provides a 64-bit decryptor, as the ransomware is also a 64-bit and can’t run on 32-bit Windows. If you have no choice but to use 32-bit applications, you may download 32-bit decryptor here.
Avast released both a 64-bit decryptor and a 32-bit Windows decryptor.
Victims have to provide a pair of files, one encrypted by the Akira ransomware and its original files
“On the following page, you need to supply an example of a file in its original form and then one encrypted by Akira ransomware. Type both names of the files. You can also drag & drop files from Windows Explorer to the wizard page.” states Avast. “It is extremely important to pick a pair of files that are as big as you can find. Due to Akira’s block size calculation, there may be dramatic difference on the size limit even for files that differ by a size of 1 byte.”
The decryptor also supports the option to back up encrypted files, which is recommended by the security firm.
Avast is working to create a decryptor for the Linux variant, meantime it has released IOCs (indicators of compromise) for both Windows and Linux variants.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Akira ransomware)
The post Avast released a free decryptor for the Windows version of the Akira ransomware appeared first on Security Affairs.