Industrial cybersecurity firm Dragos revealed that a ransomware group attempted to breach its infrastructure and extort it.
Industrial cybersecurity firm Dragos revealed that on May 8, 2023, a known ransomware group attempted and failed to breach the company systems.
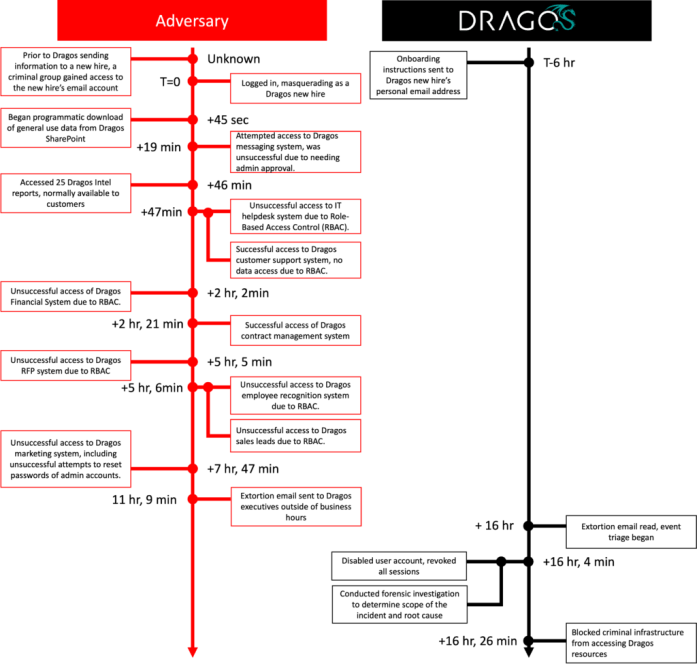
The cybercriminals compromised the personal email address of a new sales employee prior to his/her start date, and used the obtained personal information to impersonate the Dragos employee and accomplish the initial steps in the employee onboarding process.
The intruders had access to resources that are usually available to new employees in the sales department. The attackers were able to access SharePoint and the Dragos contract management system.
In one instance, the attackers were able to access a report with IP addresses associated with a customer, however, Dragos immediately informed the customer.
The company pointed out that the attackers did not compromise its network or the Dragos Platform.
“We investigated alerts in our corporate Security Information & Event Management (SIEM) and blocked the compromised account. We promptly activated our incident response retainer with a leading service provider and engaged our third-party Monitoring, Detection & Response (MDR) provider to manage incident response efforts.” reads the statement published by the company. “We are confident that our layered security controls prevented the threat actor from accomplishing what we believe to be their primary objective of launching ransomware.”
The company states that the security controls in place have prevented threat actors from performing malicious activities (i.e. lateral movement, escalating privileges, establishing persistent access, or making any changes to the infrastructure) once gained a foothold in its network.
Below is the timeline of the attack shared by the industrial cybersecurity firm.
According to the statement, the cybercriminal group failed to deploy ransomware, then pivoted to attempting to extort the company to avoid public disclosure.
The group sent various messages and an extortion email to Dragos executives, but the company avoided getting in touch with the criminals.
Shortly after reading the extortion message, the security team disabled the compromised account and locked out the attackers. The security firm confirmed that an investigation is still ongoing.
“While the external incident response firm and Dragos analysts feel the event is contained, this is an ongoing investigation. The data that was lost and likely to be made public because we chose not to pay the extortion is regrettable.” concludes the statement. “However, it is our hope that highlighting the methods of the adversary will help others consider additional defenses against these approaches so that they do not become a victim to similar efforts.”
The company also shared Indicators of Compromise (IoCs) for this attack.
We are in the final!
Please vote for Security Affairs (https://securityaffairs.com/) as the best European Cybersecurity Blogger Awards 2022 – VOTE FOR YOUR WINNERS
Vote for me in the sections where is reported Securityaffairs or my name Pierluigi Paganini
Please nominate Security Affairs as your favorite blog.
Nominate Pierluigi Paganini and Security Affairs here here: https://docs.google.com/forms/d/e/1FAIpQLSepvnj8b7QzMdLh7vWEDQDqohjBUsHyn3x3xRdYGCetwVy2DA/viewform
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, ICS)
The post Cybersecurity firm Dragos shared details about a failed extortion attempt it suffered appeared first on Security Affairs.