Threat actors were observed installing the abandoned Eval PHP plugin on compromised WordPress sites for backdoor deployment.
Researchers from Sucuri warned that threat actors are installing the abandoned Eval PHP plugin on compromised WordPress sites for backdoor deployment.
The Eval PHP plugin allows PHP code to be inserted into the pages and posts of WordPress sites and then executed every time the posts are opened.
The malicious code uses the file_put_contents function to create a PHP script into the docroot of the website with the specified remote code execution backdoor. The backdoor will be injected into the file structure when threat actors visit one of the infected posts or pages.
The experts pointed out that the plugin hasn’t been updated in over a decade and the number of real active installs is very low. Since the beginning of April threat actors are installing the Eval PHP plugin on compromised WordPress sites and using it to inject malicious PHP code into web pages.
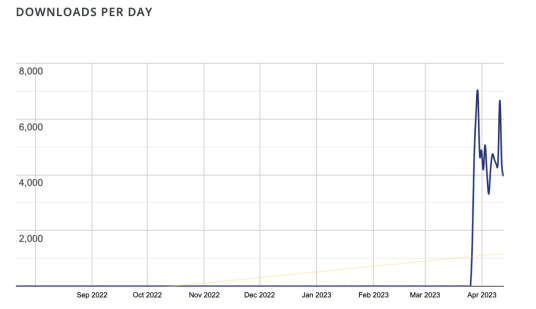
During the last ten years, since the end of March, 2023, the plugin rarely had 1 download a day. Around March 29, the researchers observed daily downloads spike to 7,000. Then, every single day the plugin totaled 3k-5k downloads, while the total number of downloads reached 100,000.
The Eval PHP plugin continues to be available through the WordPress repository, Sucuri explained.
The cause of the surge of downloads is the hacking campaign conducted by the threat actors.
Sucuri reported that all the requests originate from three IP addresses, 91[.]193[.]43[.]151, 79[.]137[.]206[.]177, 212[.]113[.]119[.]6.
The experts explained that the PHP backdoor can hide requests as cookies to avoid detection.
“Since the backdoor uses the $_REQUEST[id] to obtain the executable PHP code, it doesn’t require a POST request to conceal its parameters in access logs — it can pass them as cookies, since $_REQUEST contains the contents of $_GET, $_POST and $_COOKIE.” reads the post published by Sucuri. “GET requests without visible parameters look less suspicious than POST requests. But in the case of this backdoor, GET can be equally dangerous.”
In the attacks observed by Sucuri, threat actors successfully log into WordPress admin and created malicious pages using the real site administrator.
On some of the compromised sites, the experts observed the presence of malicious admin users with random names and outlook.com emails.
The experts explained that old and abandoned plugins that are still present in the official repository pose a security risk.
“Keeping such plugins in the official repository makes it easier for hackers to stay under radar since they can install a legitimate unmodified plugin from a reputable source instead of installing fake plugins or modifying existing plugins, which can be detected by scanners that monitor integrity of known plugins.” Sucuri concludes.
Please vote for Security Affairs (https://securityaffairs.com/) as the best European Cybersecurity Blogger Awards 2022 – VOTE FOR YOUR WINNERS
Vote for me in the sections:
- The Teacher – Most Educational Blog
- The Entertainer – Most Entertaining Blog
- The Tech Whizz – Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: https://docs.google.com/forms/d/e/1FAIpQLSfaFMkrMlrLhOBsRPKdv56Y4HgC88Bcji4V7OCxCm_OmyPoLw/viewform
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, WordPress)
The post Abandoned Eval PHP WordPress plugin abused to backdoor websites appeared first on Security Affairs.