North Korea-linked APT group Lazarus employed new Linux malware in attacks that are part of Operation Dream Job.
North Korea-linked APT group Lazarus is behind a new campaign tracked as Operation DreamJob (aka DeathNote or NukeSped) that employed Linux malware.
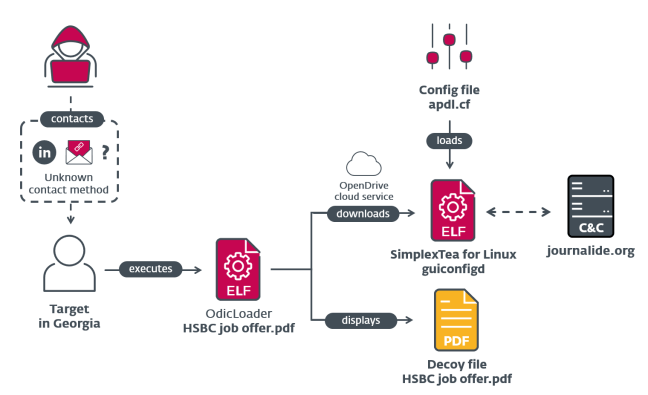
The threat actors were observed using social engineering techniques to compromise its targets, with fake job offers as the lure.
ESET researchers detailed the full attack chain that commences with spear-phishing or direct messages on LinkedIn delivering a ZIP file containing a fake HSBC job. The archive contains a native 64-bit Intel Linux binary written in Go and named HSBC job offer?pdf.
“Interestingly, the file extension is not .pdf. This is because the apparent dot character in the filename is a leader dot represented by the U+2024 Unicode character. The use of the leader dot in the filename was probably an attempt to trick the file manager into treating the file as an executable instead of a PDF.” reads the analysis published by ESET. “This could cause the file to run when double-clicked instead of opening it with a PDF viewer.”
Upon executing the file, the attackers display a decoy PDF user using xdg-open. The experts tracked dubbed the ELF downloader OdicLoader, it fetches the second-stage backdoor SimplexTea from OpenDrive.
ESET researchers added that the analysis of recent attacks revealed similarities between artifacts used in the Dream Job campaign and those employed as part of the 3CX supply chain attack.
One of the pieces of evidence that corroborates the attribution to the Lazarus APT is the domain journalist [.] org which was one of the four C2 servers used to control the malware used in the 3CX attack.
The experts speculate that the supply chain attack has been prepared since December 2022, when the attackers gained a foothold inside 3CX’s network.
“It is also interesting to note that Lazarus can produce and use malware for all major desktop operating systems: Windows, macOS, and Linux. Both Windows and macOS systems were targeted during the 3CX incident, with 3CX’s VoIP software for both operating systems being trojanized to include malicious code to fetch arbitrary payloads. In the case of 3CX, both Windows and macOS second-stage malware versions exist. This article demonstrates the existence of a Linux backdoor that probably corresponds to the SIMPLESEA macOS malware seen in the 3CX incident.” concludes the report. “We named this Linux component SimplexTea and showed that it is part of Operation DreamJob, Lazarus’s flagship campaign using job offers to lure and compromise unsuspecting victims.”
Please vote for Security Affairs (https://securityaffairs.com/) as the best European Cybersecurity Blogger Awards 2022 – VOTE FOR YOUR WINNERS
Vote for me in the sections:
- The Teacher – Most Educational Blog
- The Entertainer – Most Entertaining Blog
- The Tech Whizz – Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: https://docs.google.com/forms/d/e/1FAIpQLSfaFMkrMlrLhOBsRPKdv56Y4HgC88Bcji4V7OCxCm_OmyPoLw/viewform
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Lazarus)
The post Lazarus APT group employed Linux Malware in recent attacks and was linked to 3CX supply chain attack appeared first on Security Affairs.