Files leaked by Russian IT contractor NTC Vulkan show that Russia-linked Sandworm APT requested it to develop offensive tools.
Documents leaked from Russian IT contractor NTC Vulkan show it was likely involved in the development of offensive tools. The documents demonstrate that it also developed hacking tools for the Russia-linked APT group Sandworm.
The Sandworm group (aka BlackEnergy, UAC-0082, Iron Viking, Voodoo Bear, and TeleBots) has been active since 2000, it operates under the control of Unit 74455 of the Russian GRU’s Main Center for Special Technologies (GTsST).
The group is also the author of the NotPetya ransomware that hit hundreds of companies worldwide in June 2017. In 2022, the Russian APT used multiple wipers in attacks aimed at Ukraine, including AwfulShred, CaddyWiper, HermeticWiper, Industroyer2, IsaacWiper, WhisperGate, Prestige, RansomBoggs, and ZeroWipe.
A joint research conducted by Mandiant with a collective of media outlets (including Papertrail Media, Der Spiegel, Le Monde, and Washington Post) focused on documents, dated between 2016 and 2020, belonging to NTC Vulkan (Russian: ??? ??????).
“The documents detail project requirements contracted with the Russian Ministry of Defense, including in at least one instance for GRU Unit 74455, also known as Sandworm Team. These projects include tools, training programs, and a red team platform for exercising various types of offensive cyber operations, including cyber espionage, IO, and operational technology (OT) attacks.” reads the report published by Mandiant.
The documents show that the Russian company is a contractor for Russian intelligence, including the Main Intelligence Directorate of the General Staff of the Armed Forces of the Russian Federation (GRU) Sandworm group. The company was commissioned for the development of tools, training programs, and a hacking platform.
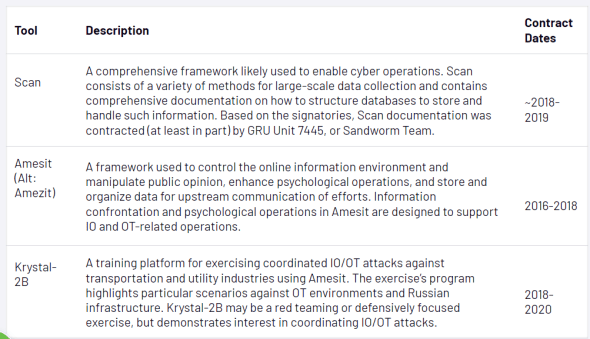
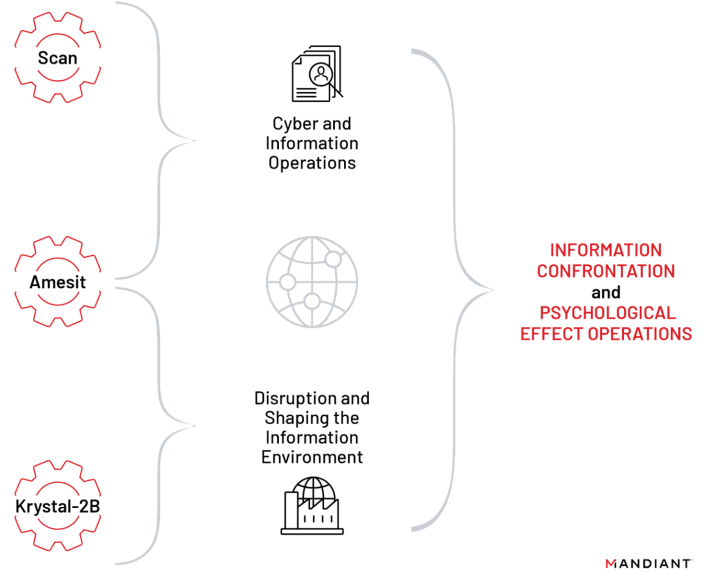
Mandiant states that NTC Vulkan has held contracts with Russian intelligence services on projects to enable cyber and IO operations. The documents include details for three projects named Scan, Amesit, and Krystal-2B.
“Mandiant did not identify any evidence indicating how or when the tools could be used. However, based on our analysis of the capabilities, we consider it feasible that the projects represent only some pieces of a variety of capabilities pursued by Russian-sponsored actors to conduct different types of cyber operations.” continues the report.
Scan is a comprehensive framework that allows operators to gather different types of information such as network details, configurations, and vulnerabilities, among other types of data, to enable cyber operations.
Amesit and Krystal-2B focus on developing the capability to control the information environment. The former could be used to manipulate public opinion and the latter was designed to simulate IT/OT attacks.
“These projects also show interest in holistic operations to conduct information control and/or confrontation and amplify the psychological effects of cyber operations. For example, Amesit and Krystal-2B demonstrate a high value placed on the psychological impact of offensive cyberattacks, specifically OT operations, by highlighting the role of information operations in determining the impact of an ICS incident.” continues Mandiant. “The combination of different tactics in cyber operations is familiar to Russian cyber operations”
Experts warn that the documents related to Krystal-2B and Amesit projects also demonstrates the interest in critical infrastructure targets of Russia-linked threat actors. Energy utilities and oil and gas, but also water utilities and transportation systems, are privileged targets of nation-state actors.
“As we continue to observe the intensification of threat activity from Russian-sponsored actors in parallel to the invasion in Ukraine, defenders should remain aware about the capabilities and priorities reflected in these documents to be prepared for protecting critical infrastructure and services.” concludes the report.
Please vote for Security Affairs (https://securityaffairs.com/) as the best European Cybersecurity Blogger Awards 2022 – VOTE FOR YOUR WINNERS
Vote for me in the sections:
- The Teacher – Most Educational Blog
- The Entertainer – Most Entertaining Blog
- The Tech Whizz – Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: https://docs.google.com/forms/d/e/1FAIpQLSfaFMkrMlrLhOBsRPKdv56Y4HgC88Bcji4V7OCxCm_OmyPoLw/viewform
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, NTC Vulkan)
The post Leaked documents from Russian firm NTC Vulkan show Sandworm cyberwarfare arsenal appeared first on Security Affairs.