Researchers discovered malware-laced installers for the TOR browser that is spreading clipper malware in Russia and Eastern Europe.
Kaspersky researchers discovered a Trojanized version of the Tor Browser that is spreading a clipper malware in Russia and Eastern Europe. The attackers take advantage of the fact that the official Tor Project has been banned in Russia since the end of 2021, so users in Russia search for third-party repositories to download the Tor browser. According to the metrics provided by the Tor Project, Russia was the second largest country by the number of Tor users in 2021 (with over 300,000 daily users, or 15% of all Tor users). Malware authors have created trojanized Tor Browser bundles and are distributing them among Russian-speaking users.
The first variant of the rogue version of the browser appeared in the threat landscape in December 2021, but experts pointed out that since August 2022 they observed a wave of torbrowser_ru.exe malicious executables. The malicious installers offered Tor Browser with a regional language pack, including Russian.
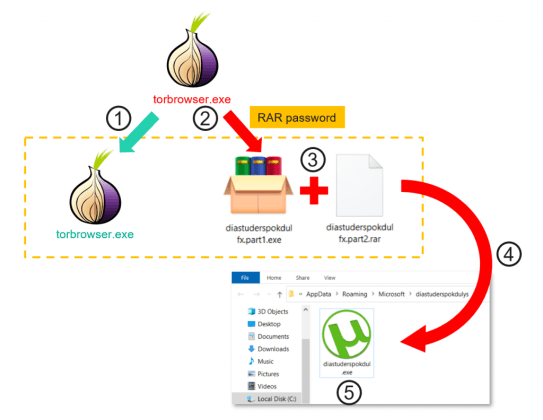
The victims download the Tor Browser from a third-party server and execute it as torbrowser.exe. The researchers noticed that the installer is not digitally signed, it is just a RAR SFX (self-extracting executable) archive.
The archive contains the following files:
- The original torbrowser.exe installer with a valid digital signature from the Tor Project.
- A command-line RAR extraction tool with a randomized name.
- A password-protected RAR archive (random password).
Upon executing the SFX, the original torbrowser.exe and the RAR extraction tool are launched on the embedded password-protected RAR archive. The archive is password-protected to evade detection.
“It doesn’t protect the malware from sandbox-based detection. The password and the destination for the extraction are part of the trojanized torbrowser.exe executable, and may be extracted via manual analysis.” reads the analysis published by Kaspersky. “Once the file is dropped inside one of the current user AppData subdirectories, the dropped executable is started as a new process and registers itself in the system autostart. Most of the time, the executable is disguised with the icon of a popular application, such as uTorrent.”
The clipper employed in the attacks is protected with the commercial software protector Enigma packer v4.0. The malware authors likely used a cracked version of the commercial packer.
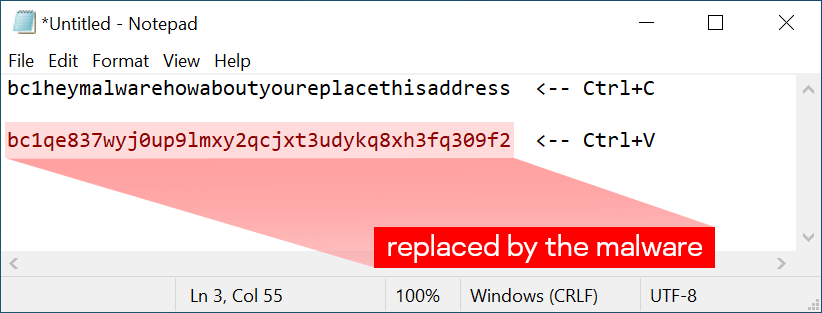
The payload is quite simple, it monitors the Windows clipboard, and when the clipboard contains text, it scans the contents with a set of embedded regular expressions to replace the included wallet address with one randomly chosen address from a hardcoded list.
The malware also supports a feature to disable itself through a special hotkey combination (Ctrl+Alt+F10), this option was likely added during the testing phase.
The researchers detected 16,000 samples, most of them registered in Russia and Eastern Europe. The malware spread to at least 52 countries worldwide. Below are the TOP 10 affected countries:
- Russia
- Ukraine
- United States
- Germany
- Uzbekistan
- Belarus
- China
- Netherlands
- United Kingdom
- France
Kaspersky analyzed the cryptowallet replacement addresses and determine that the threat actors behind the attacks have earned almost $381K worth of Bitcoin, $10K in Litecoin, and $5K Ether. The experts were not able to determine the amount of Monero cryptocurrencies stolen by the threat actors due to the privacy features supported by the cryptocurrency scheme.
“A mistake likely made by all victims of this malware was to download and run Tor Browser from a third-party resource. We haven’t managed to identify a single website that hosts the installer, so it is likely distributed either via torrent downloads or some other software downloader. The installers coming from the official Tor Project were digitally signed and didn’t contain any signs of such malware. So, to stay safe, in the first place, download software only from reliable and trusted sources.” concludes the report. “However, even if you do download a rogue file masked as something else, using a decent antivirus solution or uploading the file to VirusTotal could help identify any malicious intent”
If you want to have full confidence that your system was not infected with clipper malware copy a wallet address and paste it into a text document. If the original wallet differs from the pasted one your system is infected.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Tor Browser)
The post Clipper attacks use Trojanized TOR Browser installers appeared first on Security Affairs.