Intezer researchers reported that a South Asian espionage group, tracked as Bitter, is targeting the Chinese nuclear energy industry.
Intezer researchers uncovered a cyberespionage campaign targeting the Chinese nuclear energy sector, they linked it to the Bitter APT group.
The Bitter APT group is a South Asian cyberespionage group active since at least 2021. The group focuses on energy and government sectors, in the past, the group targeted organizations in Pakistan, China, Bangladesh, and Saudi Arabia.
In recent attacks, experts noted updates to the first-stage payloads and the implementation of new layers of obfuscation to avoid detection. Threat actors also employed additional decoys for social engineering.
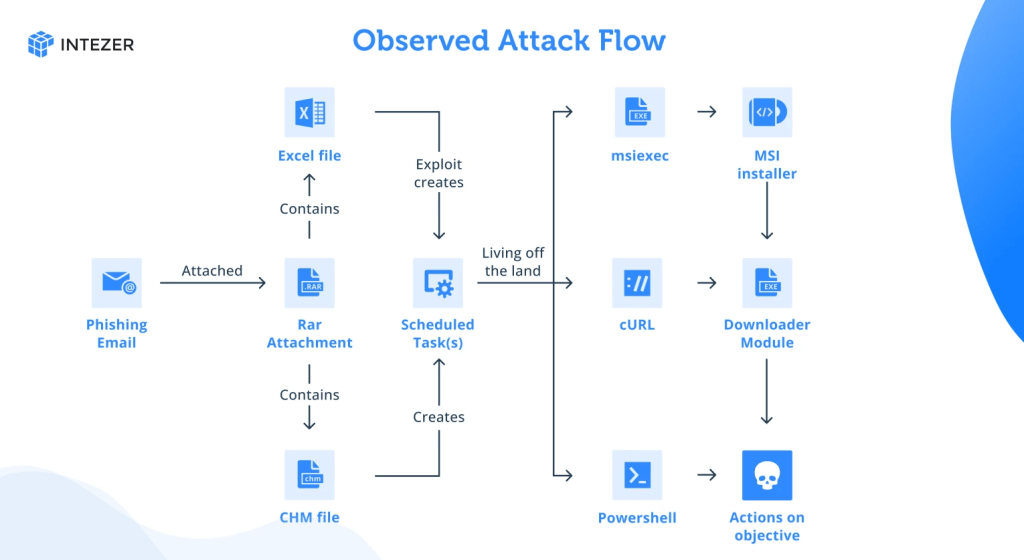
Experts identified seven phishing emails that were used in the phishing campaign aimed at recipients in China’s nuclear energy industry. The phishing messages impersonated the Embassy of Kyrgyzstan in China, inviting them to join conferences on subjects that are relevant to the recipients.
“We identified seven emails pretending to be from the Embassy of Kyrgyzstan, being sent to recipients in the nuclear energy industry in China. In some emails, people and entities in academia are also targeted, also related to nuclear energy. The phishing emails contain a lure that invites the recipients to join conferences on subjects that are relevant to them.” reads the report published by Intezer. “The lures are designed to socially engineer the recipient to download and open an attached RAR file that contains either a Microsoft Compiled HTML Help (CHM) or Excel payload.”
The messages attempt to trick recipients into opening an attached RAR archive that contains CHM or Excel payloads created to achieve persistence and fetch additional payloads from the C2.
“The Excel payloads simply contain an Equation Editor exploit that creates two different scheduled tasks. There is no decoy in the document.” contnues the report. “One scheduled task (shown below) runs every 15 minutes, to download a next stage EXE payload using cURL, also sending the actor the name of the infected machine. These tactics have been observed being used by Bitter APT in 2021/2022.”
The most common files used by the APT group are the CHM files, they can be used to execute arbitrary code with low user interaction.
One of the variants identified by Intezer created a scheduled task to execute a remote MSI payload using msiexec. Intezer experts were able only to retrieve empty MSI files, that were likely used for reconnaissance and which could be replaced with an actual payload if the target looks promising.
Another version of the CHM file analyzed by the experts was performing a similar activity through an encoded PowerShell command stage.
“Bitter APT have been conducting espionage campaigns for years using many tactics, including phishing, to achieve their goals. It is advised that entities in government, energy, and engineering especially those in the Asia-Pacific region should remain vigilant when receiving emails, especially those claiming to be from other diplomatic entities.” Intezer concludes.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Bitter APT)
The post Bitter APT group targets China’s nuclear energy sector appeared first on Security Affairs.