Cisco Talos researchers published PoC exploits for vulnerabilities in Netgear Orbi 750 series router and extender satellites.
Netgear Orbi is a line of mesh Wi-Fi systems designed to provide high-speed, reliable Wi-Fi coverage throughout a home or business. The Orbi system consists of a main router and one or more satellite units that work together to create a seamless Wi-Fi network that can cover a large area with consistent, high-speed Wi-Fi.
One of the key benefits of the Orbi system is its use of mesh networking technology, which allows the satellite units to communicate with the main router and with each other to provide strong Wi-Fi coverage throughout the home or business.
Cisco worked with Netgeat to solve the issues and is disclosing them according to its 90-day timeline outlined in Cisco’s vulnerability disclosure policy.
Cisco Talos researchers published Proof-of-concept (PoC) exploits for multiple vulnerabilities in Netgear’s Orbi 750 series router and extender satellites.
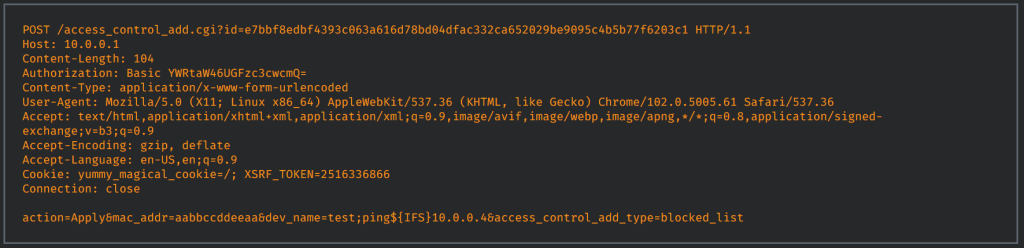
The experts discovered four vulnerabilities in the Netgear Orbi mesh wireless system, the most critical one is a critical remote code vulnerability, tracked as CVE-2022-37337 (CVSS v3.1: 9.1), that resides in the access control functionality of the Netgear Orbi router.
“A command execution vulnerability exists in the access control functionality of Netgear Orbi Router RBR750 4.6.8.5.” states Talos. “An attacker can make an authenticated HTTP request to trigger this vulnerability.”
A threat actor can exploit the flaw by sending a specially crafted HTTP request.
“Talos discovered a vulnerability in the Orbi Satellite — TALOS-2022-1596 (CVE-2022-37337) — that could lead to arbitrary command execution on the device. The user needs to authenticate into the mesh system first, meaning they’d need to access an unprotected network or the login credentials of a password-protected network, for this attack to be successful. Then, the adversary needs to send a specially crafted HTTP request to trigger the vulnerability.” reads the advisory published by Cisco Talos.
Cisco published a Proof of Concept exploit for this issue:
Below is the timeline for this issue that was reported by Dave McDaniel of Cisco Talos:
2022-08-30 – Initial Vendor Contact
2022-09-05 – Vendor Disclosure
2023-01-19 – Vendor Patch Release
2023-03-21 – Public Release
Another two issues discovered by the researchers are respectively tracked TALOS-2022-1595 (CVE-2022-38452) and TALOS-2022-1597 (CVE-2022-36429). The flaws impacts the main Orbi router, their exploitation can lead to arbitrary command execution if the attacker sends a specially crafted network request or JSON object, respectively.
The last flaw discovered by Talos is tracked as TALOS-2022-1598 (CVE-2022-38458), an attacker can exploit these flaws to carry out a man-in-the-middle attack to trick the service’s Web Services Management tool into disclosing sensitive information.
Netgear addressed the flaws with the release of the firmware version 4.6.14.3 on January 19, 2023.
The security firm is not aware of attacks in the wild exploiting these flaws.
“Users are encouraged to update these affected products as soon as possible: Netgear Orbi Satellite RBS750, version 4.6.8.5. Talos tested and confirmed these versions of the Orbi system could be exploited by these vulnerabilities.” concludes the advisory.
The company also released Snort rules (60474 – 60477 and 60499) to detect exploitation attempts against this vulnerability.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Netgear Orbi)
The post Experts released PoC exploits for severe flaws in Netgear Orbi routers appeared first on Security Affairs.