Cyber security researcher Luca Mella analyzed the Makop ransomware employed in a recent intrusion.
Executive summary
- Insights from a recent intrusion authored by Makop ransomware operators show persistence capability through dedicated .NET tools.
- Makop toolkit includes both off-the-shelf tools and custom-developed ones, including tools from the Chinese underground ecosystem.
- Makop gang did not conduct any significative retooling since 2020, which is a clear indicator of their effectiveness even after three years and hundreds of successful compromises.
- The gang leverages exposed remote administration services and internet-facing vulnerabilities to gain and maintain access to victim networks.
Introduction
The Makop ransomware operators started their infamous criminal business in 2020 leveraging a new variant of the notorious Phobos ransomware. During the last years, the gang maintained a solid presence in the criminal underground even if they did not join the double extortion practice.
Their operations are based on the human operator ransomware practice where most of the intrusion is handled by hands-on keyboard criminals, even in the encryption stage.
Makop ransomware gang is classified as a tier-B ransomware actor, but despite this, they keep hitting companies in Europe and Italy. Technical details of the Makop ransomware encryption tool have been greatly deepened by the Lifars security team (link), so, in this article, I am going to focus on other parts of the Makop gang arsenal leveraged to conduct digital extortions.
Technical Details
Makop ransomware operator arsenal is a hybrid one: it contains both cust-developed tools and off-the-shelf software taken from public repositories. In particular, recent investigations were able to identify four of them: the ARestore escalation tool, the backdoor, and other publicly available toolkits such as Advanced_Port_Scanner and a particular popular Chinese hack tool.
Custom tools
After the initial access, Makop criminals are still using an old tool dated back to their first operations in cyberspace. The “ARestore” tool is .NET executable built in 2020 and partially obfuscated. Also, the compilation time in the PE header looks time stomped, but the metadata from the .NET assembly modules reveal a more plausible date matching the time scale of the Makop operations.
filename: ARestore.exe
md5: 7f86b67ac003eda9d2929c9317025013
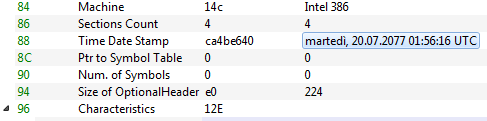
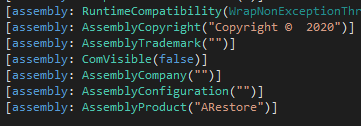
The obfuscated part of the code is based on a switch-case state-machine looping and jumping through labels in the MSIL code. Despite this, the tool does not contain any evasion or anti-debugging techniques and contains IL-only, 32-bit code.
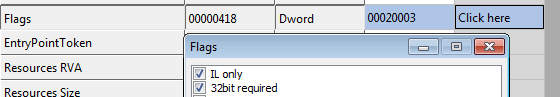
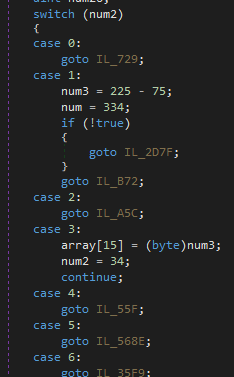
The tool is designed for two main purposes: generating comb lists of local windows user names and potential passwords, and testing them locally. The tool is able to automatically retrieve local users from groups, filter for administration, and then test the password. The crooks currently use it after the initial access phase of their attack chain.
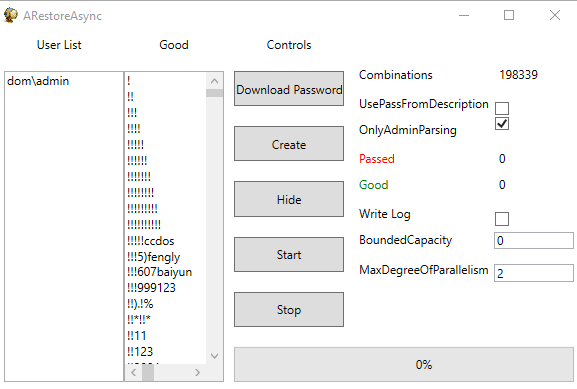
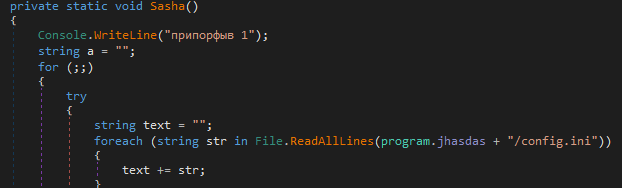
Makop operators also leverage other custom .NET assemblies to achieve further stages of the kill chain. For instance, they are using a particular persistence tool we name “PuffedUp” designed to ensure persistence after the initial access. Even this tool looks compiled and generated back in the early stage of the Makop operations and is still in use in current intrusions. Even this time the executable has been built in 2020, but it is not obfuscated at all.
filename:data.exe
md5:e245f8d129e8eadb00e165c569a14b71
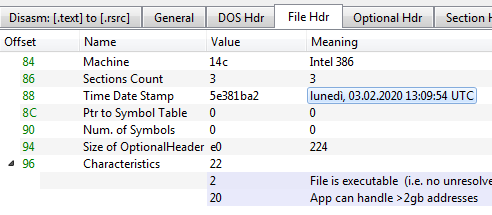
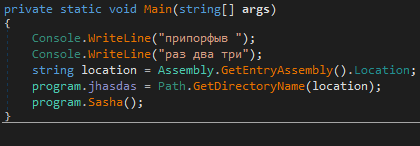
During recent Makop intrusions, the tool has been coupled with another executable named “c.exe”, but, unfortunately, it has been erased by the attackers during the disengagement phase. Anyway, a quick look at the PuffedUp code reveals a plain logic to keep its execution persistent through a RUN registry key.
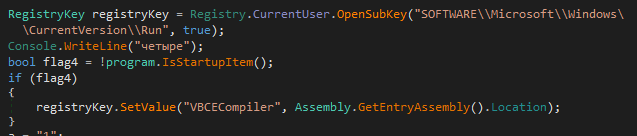
Interestingly, the tool relies on a textual configuration file placed in the same folder. This particular file contains one or more 42 chars strings, that will be placed into the user clipboard. Apparently, a weird behavior that might make sense only with a more complete view of the Makop arsenal.
Off-the-shelf tools
Makop ransomware operators extensively use off-the-shelf open-source and freeware tools to conduct lateral movement and system discovery. Along with the classical abuse of Microsoft SysInternal tools such as PsExec and other well-known open-source tools such as Putty and the never-missing Mimikatz, during recent operations, Makop abused even more peculiar software.
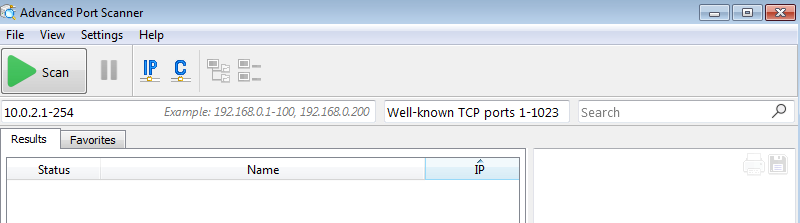
For instance “Advanced Port Scanner”, a freeware port scanning tool developed by the famous Radmin’s authors. The Makop criminals were recently using version 2.5.3869 of the tool, which dates back to 2019.
Advanced_Port_Scanner_2.5.3869.exe
md5: 6A58B52B184715583CDA792B56A0A1ED
The date of this particular version of the free software is particularly meaningful because it perfectly fits the build and compilation time of the other custom tools of the Makop intrusion arsenal. In fact, Makop criminals are still using tools built back in 2019 and 2020 to compromise small and medium enterprises around the world.
Again, another tool in the Makop arsenal still dates to 2019: the “Everything” tool. Everything is freeware software maintained by Voidtools. As anticipated, the version abused by Makop ransomware operators in recent 2023 intrusions is still version 1.4.1.932, released in January 2019.
The tool is basically a search engine for local and network shared files inside a Windows environment: unlike the default Windows search, it is designed to locate files and folders by filename instantly, speeding up system information discovery.
Filename: Everything.exe
md5: b69d036d1dcfc5c0657f3a1748608148
The last tool interesting tool spotted in the Makop arsenal is a particular system administration tool rarely used in the Russian criminal underground. Its name is YDArk and it is an open-source tool available even on GitHub (link).
filename: YDArk.exe
md5: 9fd28d2318f66e4fe37a9a5bc1637928
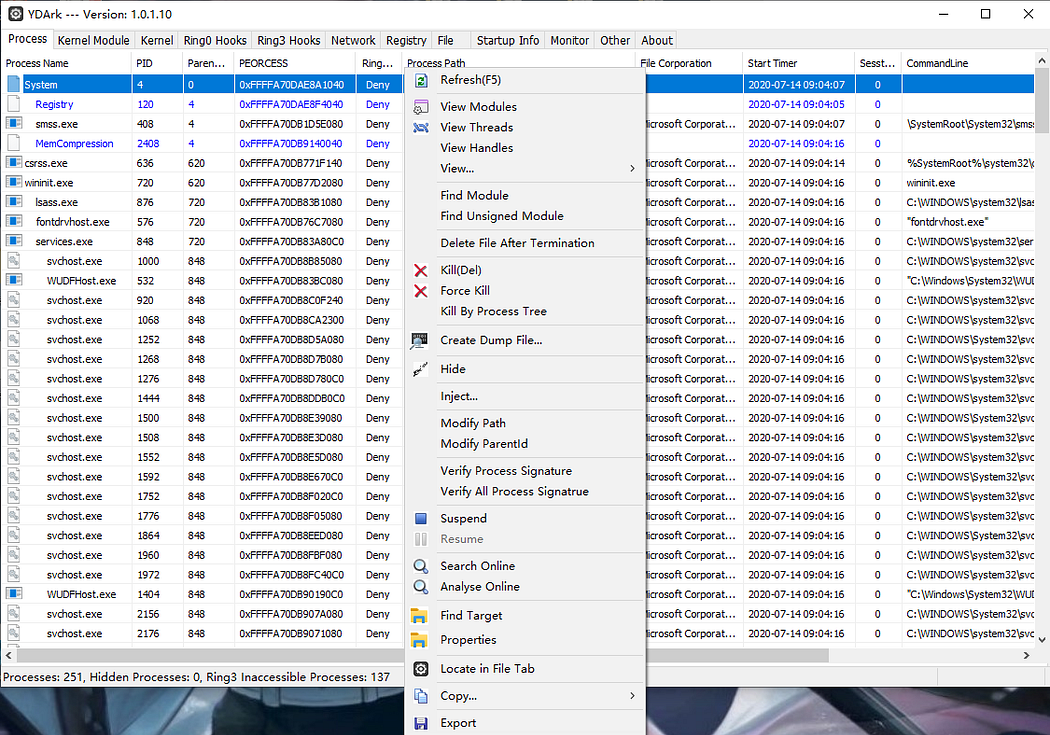
YDArk is a powerful kernel manipulation tool that appeared in the Chinese underground communities back in 2020, where it was used to evade the memory scan of the anti-cheating program in gaming communities. The tool has been previously analyzed by SangYun Shin (link). YDArk can hide processes the rootkit way: at the kernel level. It manipulates the EPROCESS kernel object of the target process by changing its PID to 0 and redirecting forward and backward ActiveProcessLinks to the self’s EPROCESS address.
The presence of this tool in the Makop arsenal is quite interesting because YDArk was previously found in other ransomware compromises:
- In April 2021 and December 2020, Sophos reported the abuse of YDArk in unspecified circumstances (link).
- In July 2022, Dark Lab security firm (link) reported the abuse of YDArk within a SonicWall SMA100 exploitation campaign aimed to leverage CVE-2019–7481 and CVE-2021–20028 on internet-exposed appliances to install Lockbit ransomware.
Conclusion
The Makop ransomware operators are conducting cyber extortion with a consistent cyber arsenal surviving detection for years. The absence of significative retooling in the Makop operator practice tells us the way to stop ransomware intrusion is still long.
If a tier-B human-operated ransomware gang targeting hundreds of companies worldwide does not need to update and change its arsenal after three years of operation it is a clear indication we are still lagging behind in enforcing an effective cyber attack deterrence strategy based on increasing the cost of attacks for cyber criminals and forcing them to retool.
The disclosure of the Makop cyber arsenal tools shall enable defenders to correlate even more intrusion attempts to the gang, to reach early detection of the abuse of both legit and custom-made tools.
Indicators of Compromise and Yara Rules are available in the original post published by Luca Mella
https://medium.com/@lcam/makop-the-toolkit-of-a-criminal-gang-53cd44563c11
About the author: Luca Mella, Cyber Security Expert, Response & Threat Intel | Manager
In 2019, Luca was mentioned as one of the “32 Influential Malware Research Professionals”. He is a former member of the ANeSeC CTF team, one of the firsts Italian cyber wargame teams born back in 2011.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Makop ransomware gang)
The post Dissecting the malicious arsenal of the Makop ransomware gang appeared first on Security Affairs.

