A new version of the Prometei botnet has infected more than 10,000 systems worldwide since November 2022, experts warn.
Cisco Talos researchers reported that the Prometei botnet has infected more than 10,000 systems worldwide since November 2022. The crypto-mining botnet has a modular structure and employs multiple techniques to infect systems and evade detection.
The Prometei botnet was first observed by Cisco Talos experts on July 2020. A deep investigation on artifacts uploaded on VirusTotal allowed the experts to determine that the botnet may have been active at least since May 2016. Experts pointed out that the malware has constantly been updated by its creators with the implementation of new modules and features.
Now Talos confirms that the Prometei botnet continues to improve modules and exhibits new capabilities in recent updates.
“More specifically, the botnet operators updated certain submodules of the execution chain to automate processes and challenge forensic analysis methods.” reads the post published by Cisco Talos. “We assess with high confidence that v3 of the Prometei botnet is of medium size, with more than 10,000 infected systems worldwide, based on data obtained by sinkholing the DGA domains over a period of one week in February 2023.”
The latest version supports previously undocumented functionalities, such as an alternative C2 domain generating algorithm (DGA), and a self-updating mechanism. The new variant also bundles version of the Apache Webserver with a web shell that’s deployed onto victim hosts.
The experts also noticed that the only excluded country in the Tor configuration is Russia, operators avoided exit nodes in other CIS countries.
The bot infected systems from 155 countries, most of the victims were observed in Brazil, Indonesia, and Turkey.
Russia only accounted for 0.31 percent of all infected systems, supporting the Talos assessment of the bot’s targeting being influenced by the Russia-Ukraine conflict based on its Tor configuration.
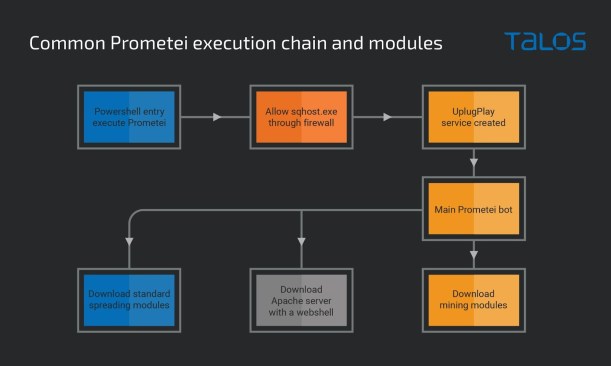
The attack chain commences by executing a PowerShell command that downloads the bot from a remote server. Then the main module retrieves the actual crypto-mining payload and other modules, it also establishes persistence on the infected systems and ensure C2 communications.
“A firewall rule named “Secure Socket Tunneling Protocol (HTTP)” is executed through the “netsh” command to add “C:\Windows\sqhost.exe” to the allowed programs list.” reads the report published by Talos. “Persistence is obtained by creating an automated system service named “UPlugPlay,” which executes sqhost.exe with the argument “Dcomsvc”. The original downloaded file is then renamed from “zsvc.exe” to “sqhost.exe.”
Some of the additional components that can be downloaded from the main module allow the bot to propagate through Server Message Block (SMB), Remote Desktop Protocol (RDP), and Secure Shell (SSH).
“Talos identified new Prometei TTPs that expand the botnet’s capabilities and, at the time of writing, have yet to be highlighted in open-source reporting.” concludes the report. “This recent addition of new capabilities aligns with threat researchers’ previous assertions that the Prometei operators are continuously updating the botnet and adding functionality.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, botnet)
The post Prometei botnet evolves and infected +10,000 systems since November 2022 appeared first on Security Affairs.