Russia-linked Sandworm APT group is behind a new Golang-based wiper, tracked as SwiftSlicer, that hit Ukraine, ESET reports.
Researchers from ESET discovered a new Golang-based wiper, dubbed SwiftSlicer, that was used in attacks aimed at Ukraine. The experts believe that the Russia-linked APT group Sandwork (aka BlackEnergy and TeleBots) is behind the wiper attacks.
The Sandworm group has been active since 2000, it operates under the control of Unit 74455 of the Russian GRU’s Main Center for Special Technologies (GTsST).
The group is also the author of the NotPetya ransomware that hit hundreds of companies worldwide in June 2017.
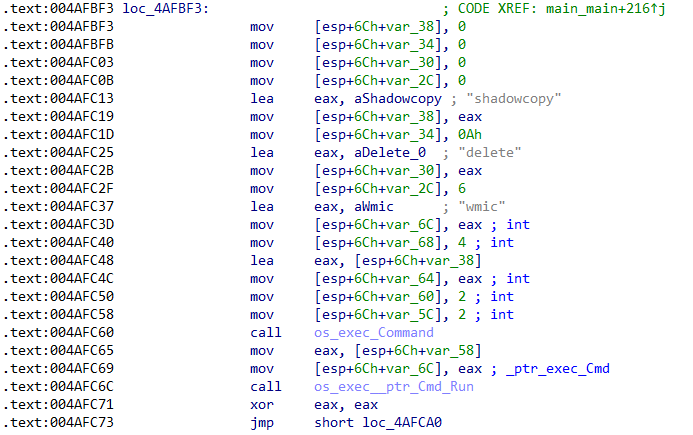
Once executed, the wiper deletes shadow copies, recursively overwrites files. The wiper targets files located in %CSIDL_SYSTEM%\drivers, %CSIDL_SYSTEM_DRIVE%\Windows\NTDS and other non-system drives before rebooting the infected system. The SwiftSlicer wiper overwriting files with 4096 bytes length blocks with randomly generated byte.
In 2022, the Russian APT used multiple wipers in attacks aimed at Ukraine, including AwfulShred, CaddyWiper, HermeticWiper, Industroyer2, IsaacWiper, WhisperGate, Prestige, RansomBoggs, and ZeroWipe.
On September 2022, the Sandworm group was observed impersonating telecommunication providers to target Ukrainian entities with malware.
Security firms warn that the Sandworm APT continues to target Ukraine with multiple means, including custom malware and botnet.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Moshen Dragon)
The post Sandworm APT targets Ukraine with new SwiftSlicer wiper appeared first on Security Affairs.

 Ukraine. Attackers deployed a new wiper we named
Ukraine. Attackers deployed a new wiper we named 