A Pro-Russian group named NoName057(16) is targeting organizations in Ukraine and NATO countries with DDoS attacks.
A Pro-Russian cybercrime group named NoName057(16) (aka 05716nnm or Nnm05716) is behind a wave of DDoS attacks against organizations in Ukraine and NATO countries, SentinelOne researchers reported.
The attacks started in March 2022 and targeted government and critical infrastructure organizations.
This week the group disrupted services across the financial sector of Denmark, and recent attacks hit organizations and businesses across Poland, Lithuania and others.
Early this month, Poland’s security agency warned of pro-Russian hackers that are continuously targeting the state since the start of the invasion of Ukraine. The security agency reported the case of the November attack on the Polish parliament that was attributed to the pro-Russian group NoName057(16).
On January 11th, SentinelLabs observed NoName057(16) begin targeting 2023 Czech presidential election candidates’ websites. The researchers identified the group operations over public Telegram channels
SentinelLabs has identified how the group operates over public Telegram channels, the researchers also identified a volunteer-fueled DDoS payment program, a multi-OS supported toolkit, and GitHub.
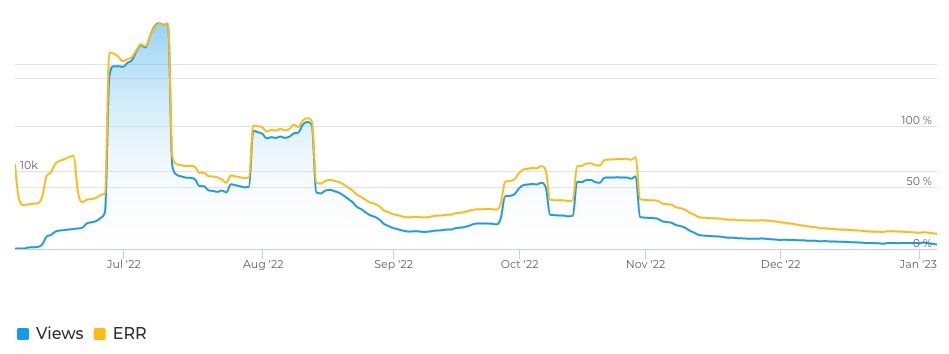
“NoName057(16) operate through Telegram to claim responsibility for their attacks, mock targets, make threats, and generally justify their actions as a group. Interestingly, NoName057(16) makes attempts to teach their followers through educational content such as explaining basic industry jargon and attack concepts.” reads the analysis published by SentinelOne. “With an average of six posts per day, the overall engagement of NoName057(16)’s Telegram efforts has slowly declined over time.”
According to the experts, the popularity of the group among followers and Telegram users is declining since July.
The group uses GitHub for its activity, such as hosting a DDoS tool website named dddosia.github[.]io (DDOSIA), and the associated GitHub repositories for hosting the latest version of their tools that are advertised in the Telegram channel. The experts noticed two GitHub profiles, dddosia and kintechi341. Early commits to the ddos_config repo were made in the name of “????? ??????????”.
GitHub removed the accounts after SentinelOne reported the abuse to the company.
The C2 infrastructure used by the group was primarily hosted on the Bulgarian telecommunications company Neterra. Experts observed threat actors also using No-IP Dynamic DNS services. The current C2 server is zig35m48zur14nel40[.]myftp.org at 31.13.195.87, which is still active.
NoName057(16) uses multiple tools to carry out their attacks. In September 2022, Avast researchers observed the group using the Bobik botnet to launch DDoS attacks.
“NoName057(16) is yet another hacktivist group to emerge following the war in Ukraine. While not technically sophisticated, they can have an impact on service availability– even when generally short lived. What this group represents is an increased interest in volunteer-fueled attacks, while now adding in payments to its most impactful contributors,” the report concludes.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, NoName057(16))
The post Pro-Russia group NoName057(16) targets Ukraine and NATO countries appeared first on Security Affairs.