Threat actors are actively exploiting a recently patched critical remote code execution (RCE) vulnerability in Control Web Panel (CWP).
Threat actors are actively exploiting a recently patched critical vulnerability, tracked as CVE-2022-44877 (CVSS score: 9.8), in Control Web Panel (CWP).
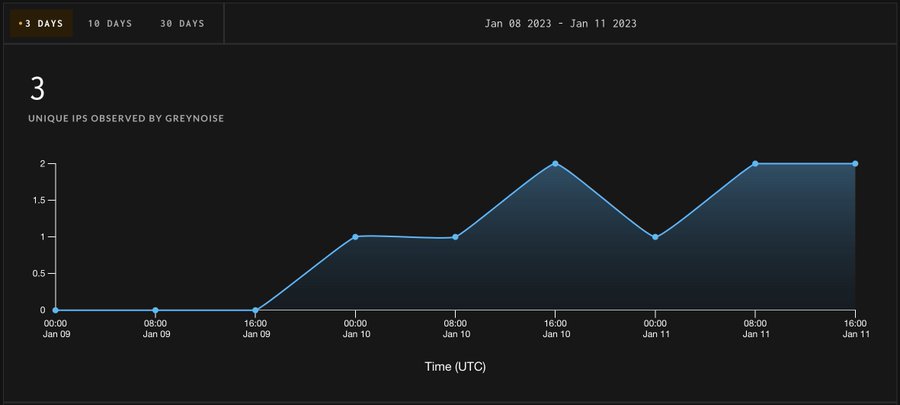
The exploitation attempts began on January 6, 2023, after a proof-of-concept (PoC) exploit code was published online.
“login/index.php in CWP (aka Control Web Panel or CentOS Web Panel) 7 before 0.9.8.1147 allows remote attackers to execute arbitrary OS commands via shell metacharacters in the login parameter.” reads the advisory for this vulnerability.
The flaw impacts the software before 0.9.8.1147, it was addressed with the release of 0.9.8.1147 version on October 25, 2022. The vulnerability was discovered by Numan Türle from Gais Security.
Researchers from Grey Noise and ShadowServer confirmed that threat actors are actively exploiting the flaw.
Users are recommended to apply the security patches immediately.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
|
try { window._mNHandle.queue.push(function (){ window._mNDetails.loadTag(“816788371”, “300×250”, “816788371”); }); } catch (error) {}
try { window._mNHandle.queue.push(function (){ window._mNDetails.loadTag(“816788371”, “300×250”, “816788371”); }); } catch (error) {}
|
(SecurityAffairs – hacking, Moshen Dragon)
The post Threat actors actively exploit Control Web Panel RCE following PoC release appeared first on Security Affairs.

 Ongoing mass exploitation of CVE-2022-44877 (Centos Web Panel 7 Unauthenticated Remote Code Execution).
Ongoing mass exploitation of CVE-2022-44877 (Centos Web Panel 7 Unauthenticated Remote Code Execution).

