Experts warn of a new variant of the Dridex banking malware that is targeting systems using the macOS operating system.
Trend Micro experts discovered a new variant of the Dridex banking malware that targets the MacOS platform and that used a new technique to deliver documents embedded with malicious macros.
The Dridex banking Trojan that has been around since 2014, it was involved in numerous campaigns against financial institutions over the years and crooks have continuously improved it. The banking malware is believed to be operated by the cybercrime gang known as Evil Corp.
The sample analyzed by Trend Micro arrived in the form of a Mach-o executable file: a.out (detected asTrojan.MacOS.DRIDEX.MANP).
The earliest sample analyzed by Trend Micro was submitted to VirusTotal in April 2019, while the most recent one is dated December 2022.
“The data segment of the sample contains the malicious embedded document and is used by the _payload_doc variable. The disassembly shows that the malware performs a loop where the content of _payload_doc is copied until the counter reaches _payload_doc_len, the size of the malicious code.” reads the analysis published by Trend Micro. “Once the malicious code is ready, the cstring segment plays a role in overwriting the code to the target files.”
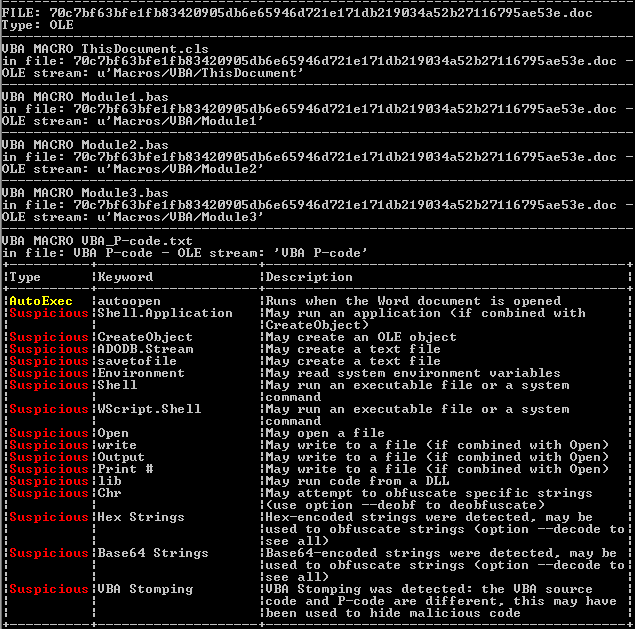
The malicious embedded document was first detected in in 2015, the researchers noticed that the affected .doc files in incorporates the ThisDocument object that includes the autoopen macro which calls the malicious functions.
The malware first searches for the .doc files in the current user (~/User/{user name}) directory using the find ~ -name “*.doc” command. It then traverses through each document file (i) using for loop, and writes the malicious code via the echo ‘%s’ command. The malicious macro code copied from the embedded document is in plain hexadecimal dump.
“While the macro feature in Microsoft Word is disabled by default, the malware will overwrite all the document files for the current user, including the clean files. This makes it more difficult for the user to determine whether the file is malicious since it doesn’t come from an external source.” continues the post.
The macros in the overwritten document connect to a remote server to retrieve additional payloads. Experts also noticed that the malware also drops an .exe file that will not run in a MacOS environment, a circumstance that suggests that the malicious code is still in the testing stage.
“While documents containing booby-trapped macros are typically delivered via social engineering attacks, the findings once again show that Microsoft’s decision to block macros by default has prompted threat actors to refine their tactics and find more efficient methods of entry.
“the malicious actors using Dridex are also trying to find new targets and more efficient methods of entry.” concludes the report. “Currently, the impact on MacOS users for this Dridex variant is minimized since the payload is an exe file (and therefore not compatible with MacOS environments). However, it still overwrites document files which are now the carriers of Dridex’s malicious macros. Furthermore, it’s possible that the threat actors behind this variant will implement further modifications that will make it compatible with MacOS.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
|
try { window._mNHandle.queue.push(function (){ window._mNDetails.loadTag(“816788371”, “300×250”, “816788371”); }); } catch (error) {}
try { window._mNHandle.queue.push(function (){ window._mNDetails.loadTag(“816788371”, “300×250”, “816788371”); }); } catch (error) {}
|
(SecurityAffairs – hacking, Dridex)
The post Dridex targets MacOS users with a new delivery technique appeared first on Security Affairs.