Russia-linked APT29 group targeted dozens of organizations and government agencies worldwide with Microsoft Teams phishing attacks.
Microsoft Threat Intelligence reported that Russia-linked cyberespionage group APT29 (aka SVR group, Cozy Bear, Nobelium, Midnight Blizzard, and The Dukes) carried out Microsoft Teams phishing attacks aimed at dozens of organizations and government agencies worldwide.
APT29 along with APT28 cyber espionage group was involved in the Democratic National Committee hack and the wave of attacks aimed at the 2016 US Presidential Elections.
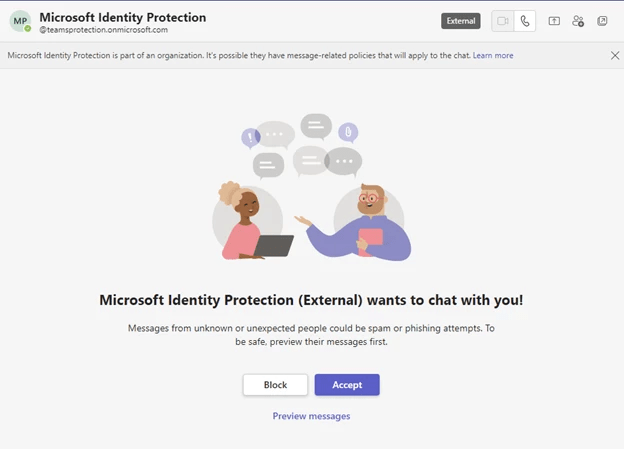
Microsoft Threat Intelligence reported that the cyberspies conducted highly targeted social engineering attacks using credential theft phishing lures sent as Microsoft Teams chat.
The attackers use previously compromised Microsoft 365 tenants owned by small businesses to create new domains that appear as technical support entities. Then the APT29 leverages Teams messages to send lures that attempt to steal credentials from a targeted organization by engaging a user and tricking it into approve multifactor authentication (MFA) prompts.
According to Microsoft, the state-sponsored hackers targeted fewer than 40 unique global organizations, including government agencies, non-government organizations (NGOs), IT services, technology, discrete manufacturing, and media sectors.
Below is the step-by-step attack chain:
The attackers send a Microsoft Teams message request to the victim, the message is sent from an external user masquerading as a technical support or security team.
Upon accepting the message request, the target user receives a Microsoft Teams message from the attacker attempting to trick them into entering a code into the Microsoft Authenticator app on their mobile device.
Once the targeted user accepted the message request and entered the code into the Microsoft Authenticator app, the attacker is granted a token to authenticate as the targeted user. Then the threat actor gains access to the victim’s Microsoft 365 account.
“The actor then proceeds to conduct post-compromise activity, which typically involves information theft from the compromised Microsoft 365 tenant. In some cases, the actor attempts to add a device to the organization as a managed device via Microsoft Entra ID (formerly Azure Active Directory), likely an attempt to circumvent conditional access policies configured to restrict access to specific resources to managed devices only.” concludes the report.
Microsoft shared Indicators of Compromise (IoCs) for these attacks and recommendations to mitigate them.
In April, 2023, Poland’s Military Counterintelligence Service and its Computer Emergency Response Team linked a recent string of attacks targeting NATO and European Union countries to the Russia-linked APT29 group
In early March, BlackBerry researchers uncovered a new cyber espionage campaign aimed at EU countries. The hackers targeted diplomatic entities and systems transmitting sensitive information about the region’s politics, aiding Ukrainian citizens fleeing the country, and providing help to the government of Ukraine.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, APT29)
The post Russian APT29 conducts phishing attacks through Microsoft Teams appeared first on Security Affairs.