Russia-linked BlueBravo has been spotted targeting diplomatic entities in Eastern Europe with the GraphicalProton Backdoor.
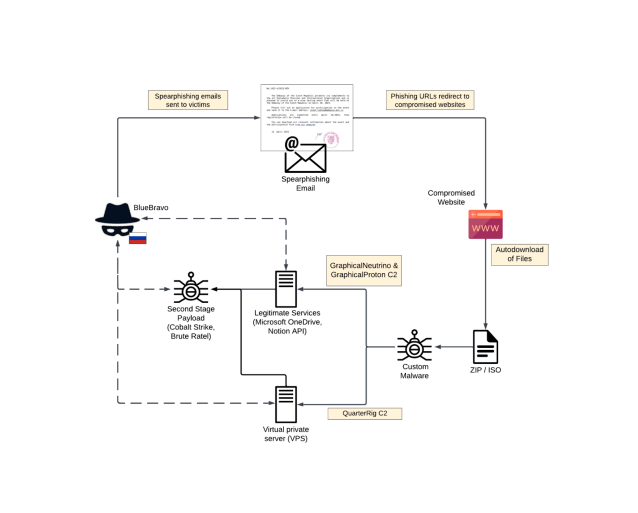
The Russia-linked threat-state actor BlueBravo (aka APT29, Cloaked Ursa, and Midnight Blizzard, Nobelium) has been observed targeting diplomatic entities throughout Eastern Europe. The group was observed conducting a spear-phishing campaign with the end goal of infecting recipients with a new backdoor called GraphicalProton. The campaign was observed between March and May 2023.
The threat actors abused legitimate internet services (LIS) for command-and-control (C2) obfuscation, expanding the range of services misused for this purpose.
On January 2023, Insikt researchers observed BlueBravo using a themed lure to deliver malware called GraphicalNeutrino. GraphicalProton is another malware in the arsenal of the group, unlike GraphicalNeutrino, which used Notion for C2, it uses Microsoft’s OneDrive or Dropbox for C2 communication.
“The group’s misuse of LIS is an ongoing strategy, as they have used various online services such as Trello, Firebase, and Dropbox to evade detection.” reads the analysis published by Recorded Future. “BlueBravo appears to prioritize cyber-espionage efforts against European government sector entities, possibly due to the Russian government’s interest in strategic data during and after the war in Ukraine.”
Both GraphicalNeutrino and GraphicalProton are used as a loader, the latter is staged within an ISO or ZIP file delivered via a phishing email.
“In May 2023, Insikt Group first described the GraphicalProton malware for clients. GraphicalProton acts as a loader, and, much like previously described samples of GraphicalNeutrino, is staged within an ISO or ZIP file and relies on the newly identified compromised domains for delivery to targeted hosts.” continues the report. “Unlike some previously analyzed samples of GraphicalNeutrino that employed Notion for C2, we observed that the newly identified GraphicalProton samples use Microsoft OneDrive instead.”
The ISO files used in the attack contain .LNK files that masquerade as .PNG images of a BMW car that’s purportedly for sale. Upon clicking the file, it will start the GraphicalProton infection chain. Attackers use Microsoft OneDrive as C2 and periodically poll a folder in the storage service to fetch additional payloads.
“As the war in Ukraine continues, it is almost certain that BlueBravo will continue to consider government and diplomatic institutions high-value targets for the foreseeable future.” concludes the report. “It is likely that BlueBravo, and by extension the Russian intelligence consumers reliant on the data BlueBravo provides, views these organizations as providing strategic insight into the decision-making process of governments allied with Ukraine.”
Follow me on Twitter: @securityaffairs Facebook and Mastodon
(SecurityAffairs – hacking, Russia)
The post Russian APT BlueBravo targets diplomatic entities with GraphicalProton backdoor appeared first on Security Affairs.