The U.S. government announced up to a $10 million bounty for information linking the Clop ransomware gang to a foreign government.
The US goverment is offering up to a $10 million bounty for information linking CL0P Ransomware Gang or any other threat actors targeting U.S. critical infrastructure to a foreign government.
The bounty is covered by the U.S. State Department’s Rewards for Justice program.
Advisory from @CISAgov, @FBI: https://t.co/jenKUZRZwt
Do you have info linking CL0P Ransomware Gang or any other malicious cyber actors targeting U.S. critical infrastructure to a foreign government?
Send us a tip. You could be eligible for a reward.#StopRansomware pic.twitter.com/fAAeBXgcWA
— Rewards for Justice (@RFJ_USA) June 16, 2023
The U.S. State Department’s Rewards for Justice (RFJ) program is a government counterterrorism rewards program that offers monetary rewards for information leading to the prevention, disruption, or conviction of individuals involved in acts against U.S. interests.
The US government offers rewards for information that leads to the arrest, conviction, or location of threat actors.
Other ransomware groups have been targeted by the RFJ, including the Conti ransomware and REvil ransomware gangs.
The Clop ransomware group recently claimed to have hacked hundreds of companies globally by exploiting MOVEit Transfer vulnerability.
MOVEit Transfer is a managed file transfer that is used by enterprises to securely transfer files using SFTP, SCP, and HTTP-based uploads.
The vulnerability is a SQL injection vulnerability, it can be exploited by an unauthenticated attacker to gain unauthorized access to MOVEit Transfer’s database.
The Clop ransomware gang (aka Lace Tempest) was credited by Microsoft for the campaign that exploits a zero-day vulnerability, tracked as CVE-2023-34362, in the MOVEit Transfer platform.
The ransomware gang published an extortion note on its dark web leak site claiming to have information on hundreds of businesses.
“WE HAVE INFORMATION ON HUNDREDS OF COMPANIES SO OUR DISCUSSION WILL WORK VERY SIMPLE.” reads the message published by the gang.
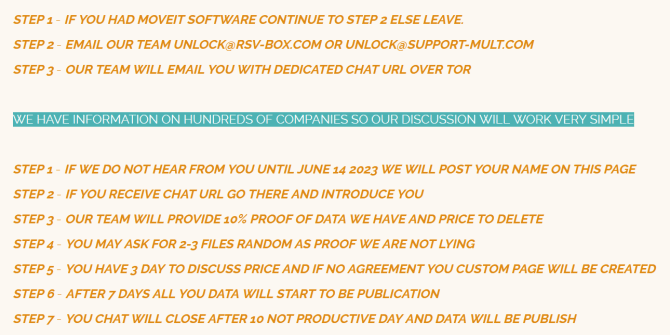
The gang urged victim organizations to contact them before their name will be added to the list of victims on the leak site. The group fixed the deadline on June 14.
At this time it is not possible to determine the exact number of organizations that were breached by the gang by exploiting the MOVEit Transfer vulnerability.
By May 31, Rapid7 experts discovered approximately 2,500 instances of MOVEit Transfer publicly accessible on the internet, with a significant portion located in the United States.
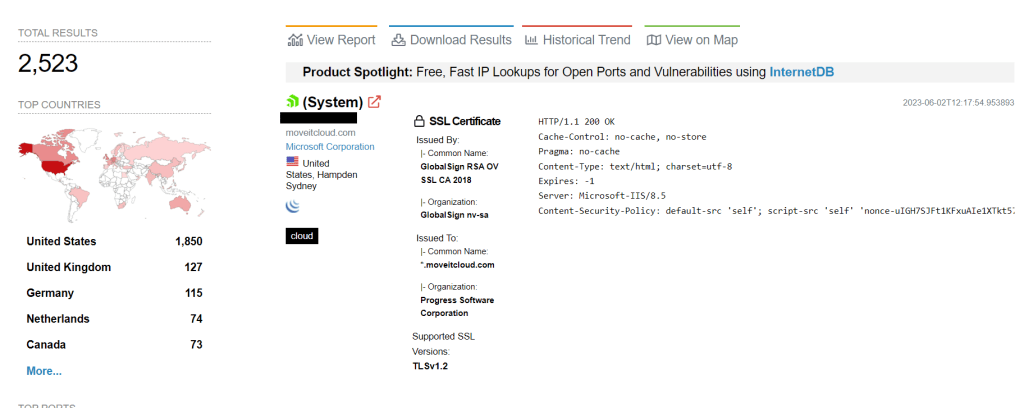
“Our teams have so far observed the same webshell name in multiple customer environments, which may indicate automated exploitation.” reported Rapid7.
Kroll researchers discovered that the Clop ransomware gang was looking for a zero-day exploit in the MOVEit software since 2021.
At the time of this writing, the Clop ransomware group already added 27 companies to the list of victims on its dark web leak site. The group claimed to have compromised the companies by exploiting the zero-day CVE-2023-34362.
According to a report published by CNN, the group has breached numerous federal agencies, including The Department of Energy.
After the publication of the report, the group published the following message on its leak site to clarify the theft of data from government agencies reported by some media:
“WE GOT A LOT OF EMAILS ABOUT GOVERNMENT DATA, WE DON’T HAVE ANY GOVERNMENT DATA AND ANYTHING DIRECTLY RESIDING ON EXPOSED AND BAD PROTECTED NOT ENCRYPTED FILE TRANSFER WE STILL DO THE POLITE THING AND DELETE ALL. ALL MEDIA SPEAKING ABOUT THIS ARE DO WHAT ALWAYS THEY DO. PROVIDE LITTLE TRUTH IN A BIG LIE. WE ALSO WANT TO REMIND ALL COMPANY THAT IF YOU PUT DATA ON INTERNET WHERE DATA IS NOT PROTECT DO NOT BLAME US FOR PENETRATION TESTING SERVICE. WE ARE ONLY FINANCIAL MOTIVATED AND DO NOT CARE ANYTHING ABOUT POLITICS.“
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Clop ransomware)
The post US govt offers $10 million bounty for info linking Clop ransomware gang to a foreign government. appeared first on Security Affairs.

