A previously undocumented APT group targets iOS devices with zero-click exploits as part of a long-running campaign dubbed Operation Triangulation.
Researchers from the Russian firm Kaspersky have uncovered a previously unknown APT group that is targeting iOS devices with zero-click exploits as part of a long-running campaign dubbed Operation Triangulation.
The experts uncovered the attack while monitoring the network traffic of its own corporate Wi-Fi network dedicated to mobile devices using the Kaspersky Unified Monitoring and Analysis Platform (KUMA).
According to Kaspersky researchers, Operation Triangulation began at least in 2019 and is still ongoing.
“The targets are infected using zero-click exploits via the iMessage platform, and the malware runs with root privileges, gaining complete control over the device and user data” reads the analysis published by Kaspersky.
Due to the difficulty of inspecting modern iOS devices internally, the researchers created offline backups of the devices to analyze. Then they used the Mobile Verification Toolkit’s mvt-ios to scrutinize the backups and ultimately collected evidence indicating traces of compromise.
The backups contain a partial copy of the filesystem, including part of the user data and service databases. By analyzing the timestamps of files, folders, and database records, the researchers were able to reconstruct a timeline of the events that occurred on the device. The researchers used the mvt-ios utility to generate a sorted timeline of the events, which is stored in a file named ‘timeline.csv.’
The analysis of the timeline revealed that the attack chains commenced with a message sent via the iMessage service to an iOS device. The message has an attachment containing an exploit. The expert explained that the message triggers a remote code execution vulnerability without any user interaction (zero-click).
The exploit used in the attack downloads multiple subsequent stages from the C2 server, including additional exploits for privilege escalation. The final payload is downloaded from the same C2 and is described by Kaspersky as a fully-featured APT platform.
Then the initial message and the exploit in the attachment are deleted.
The researchers noticed that the malicious toolset does not support persistence, likely due to the limitations of the OS. The devices may have been reinfected after rebooting.
The attack successfully targeted iOS 15.7, the analysis of the final payload has yet to be finished. The malicious code runs with root privileges, it supports a set of commands for collecting system and user information, and can run arbitrary code downloaded as plugin modules from the C2 server.
“The single most reliable indicator that we discovered is the presence of data usage lines mentioning the process named “BackupAgent”. This is a deprecated binary that should not appear in the timeline during regular usage of the device.” concludes Kaspersky. “An even less implicit indicator of compromise is inability to install iOS updates. We discovered malicious code that modifies one of the system settings file named com.apple.softwareupdateservicesd.plist. We observed update attempts to end with an error message “Software Update Failed. An error ocurred downloading iOS”.”
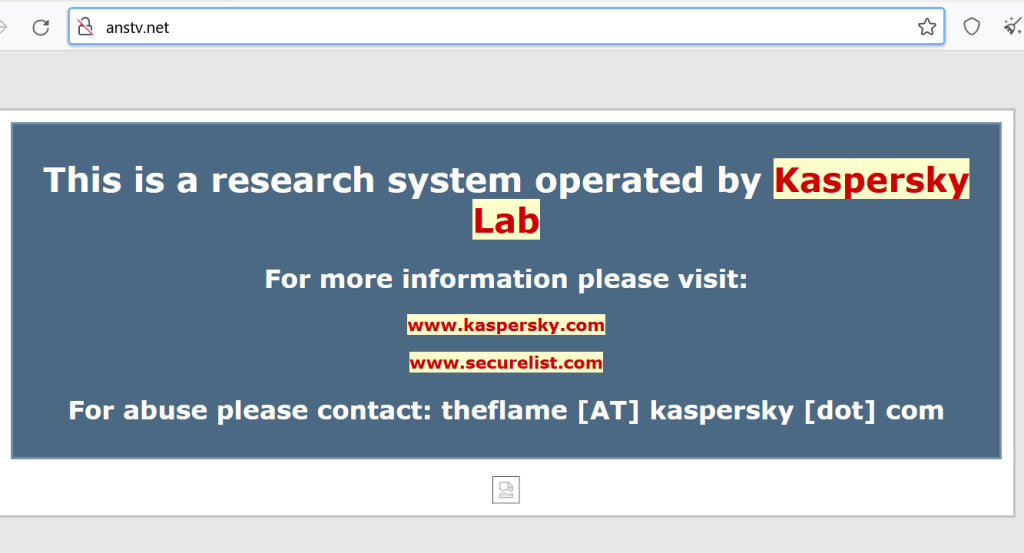
Kaspersky provided the list of C2 domains involved in the attack, at least two of them currently show the following banner:
About the author: Jurgita Lapienyt?, Chief Editor at CyberNews
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Operation Triangulation)
The post Operation Triangulation: previously undetected malware targets iOS devices appeared first on Security Affairs.

