Researchers devised an attack technique, dubbed BrutePrint Attack, that allows brute-forcing fingerprints on smartphones to bypass authentication.
Researchers have devised an attack technique, dubbed BrutePrint, that allows to brute-force fingerprints on smartphones to bypass user authentication.
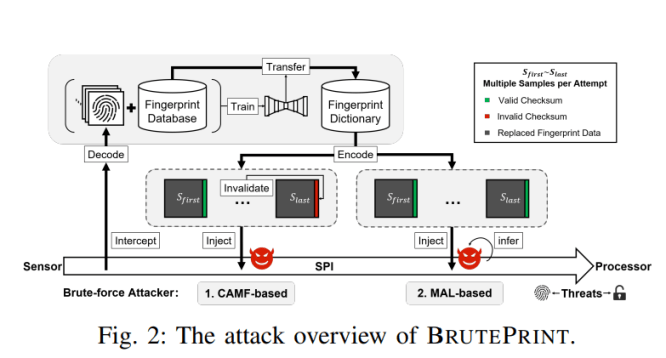
The attack technique exploits two zero-day vulnerabilities, called Cancel-After-Match-Fail (CAMF) and Match-After-Lock (MAL), in the smartphone fingerprint authentication (SFA) framework.
The BRUTEPRINT attack acts as a middleman to bypass attempt limit and hijack fingerprint images.
The two vulnerabilities exploit logical flaws in the authentication framework, stemming from inadequate protection of fingerprint data on the Serial Peripheral Interface (SPI) of fingerprint sensors.
“We find the insufficient protection of fingerprint data on the Serial Peripheral Interface (SPI) of fingerprint sensors, and thus come up with a hardware approach to do man-inthe-middle (MITM) attacks for fingerprint image hijacking” reads the research paper published by the researchers Yu Chen and Yiling He.
In order to carry out the attack, the researchers assume that:
- the attackers have physical access to the smartphone.
- the attackers possess a fingerprint database and an adversarial equipment consisting of an inexpensive printed circuit board (PCB) that intercepts data transmitted by the fingerprint sensor. In the case of certain smartphone models, the researchers utilized an adaptive flexible printed circuit (FPC). The overall cost of the equipment amounts to approximately 15 dollars.
“We implement BRUTEPRINT system to crack SFA and achieve fingerprint brute-force attack. there are two kinds of brute-force attackers who exploit CAMF and MAL vulnerabilities. Specifically, BRUTEPRINT acts as a middleman between fingerprint sensor and TEE” reads the paper. “Typically, a CAMF exploitation invalidates the checksum of transmitted fingerprint data, and a MAL exploitation infers matching results through side-channel attacks. Fingerprint image hijacking attack meets R2, which has the capability to decode the intercepted fingerprint data and encode replaced data for injection. To increase the success rate of brute-forcing, BRUTEPRINT additionally propose a fingerprint dictionary generation method that trains a neural style transfer network to transfer available fingerprint database into valid styles.”
CAMF is based on the fault-tolerant mechanisms in SFA systems, the attacker can exploit the issue to force the “Error-cancel Only” result after each authentication attempt. The experts pointed out that only “Failed” authentication result decreases the remaining attempt number restricted by the attempt limit.
This means that the attackers can make unlimited attempts if each attempt goes into the Error-cancel.
The MAL vulnerability can be exploited to make attempts to infer authentication results of fingerprint images (called the “inference attempt”) in lockout mode. The lockout mode is supported in Google’s biometric framework to penalize too many failed attempts, where no fingerprint authentication can be launched in a certain period of time or permanently.
“Although the lockout mode is further checked in Keyguard to disable unlocking, the authentication result has been made by TEE. As Success authentication result is immediately returned when a matched sample is met, it’s possible for side-channel attacks to infer the result from behaviors such as response time and the number of acquired images.” continues the report.
The researchers tested the BrutePrint attack technique against 10 popular smartphone models running the latest OS versions.
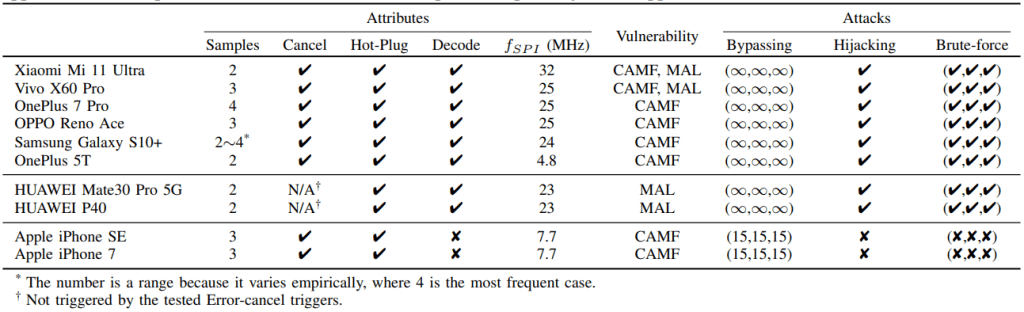
The experimental results show that attempts are made three times over the attempt limit on Touch ID, while the researchers achieved unlimited attempts on all Android devices.
“We discover vulnerabilities in SFA ecosystem that the fault-tolerant mechanism / careless userfriendly implementation can be exploited through the insecure transmission on SPI to fool the unreliable authentication algorithms. We validate the attacks on 10 representative smartphones, where all of them are affected to some extent.” concludes the paper. “With the proposed attack, adversaries can brute-force the fingerprint authentication on arbitrary victim smartphone to unlock the device and cheat many security apps. In addition, the attack method can be used to enhance presentation attacks and may also applies to other biometric systems”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, BRUTEPRINT attack)
The post BrutePrint Attack allows to unlock smartphones with brute-forcing fingerprint appeared first on Security Affairs.