A new sophisticated malware strain, dubbed DownEx, was involved in attacks aimed at Government organizations in Central Asia.
In late 2022, Bitdefender Labs researchers first observed a highly targeted cyberattack targeting foreign government institutions in Kazakhstan that involved a new sophisticated strain of malware dubbed DownEx. Later the researchers detected another attack in Afghanistan that allowed them to collect additional samples of this malware.
The researchers noticed that the malware does not share any code similarities with previously known malware families, they also reported that the domain and IP addresses involved in the attacks were not involved in any previously documented incidents.
The level of sophistication of the malware and the nature of the target suggests that the threat actor behind DownEx is a Russian state-sponsored group.
“Despite trying various methods, we have been unable to attribute these attacks to a specific threat actor. One clue pointing at the origin of the attack is the use of a cracked version of Microsoft Office 2016 popular in Russian-speaking countries (known as “SPecialisST RePack” or “Russian RePack by SPecialiST). It is also unusual to see the same backdoor written in two languages – this practice was previously observed with group APT28 (Russian-based) with their backdoor Zebrocy.” reads the report published by “Based on a combination of indicators we are attributing this campaign to a group associated with Russia, albeit with low confidence.”
The threat actors sent spear-phishing messages with diplomat-themed lure documents. The attackers used executable files posing as Microsoft Word document. The experts noticed that the attachment was simply named “! to embassy kazakh 2022.exe” and used the icon image associated with docx files.
The executable is a self-contained archive that once executed will extract two files. One of the files is the bait document, while the other one is an HTA file named log extension with embedded VBScript code
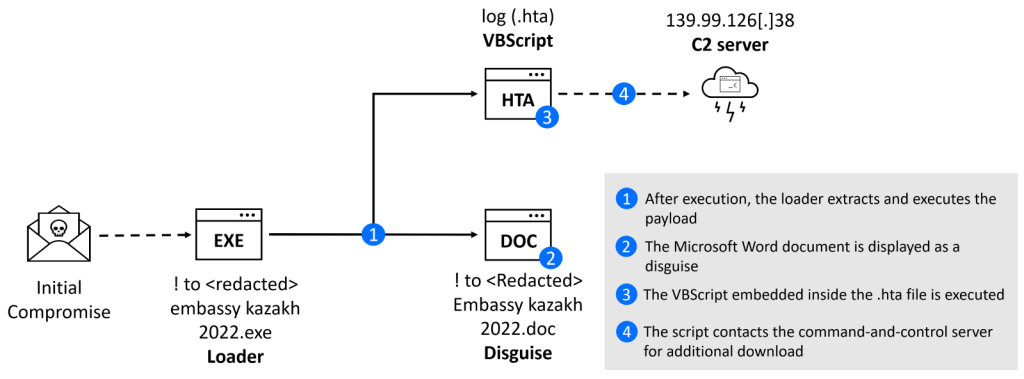
The HTA file contacts the C2 server to fetch a second-stage payload. BitDefender states that the download of the next stage failed, and they were not able to retrieve the payload from the C2 server.
“Based on our analysis of similar attacks, we expect threat actors tried to download backdoor to establish persistence.” continues the report. “Several other tools located on the victim’s machine were used to establish connection to the C2 server”
Threat actors also used multiple custom tools, including two tools written in C/C++ designed to numerate all the resources on a network, a Python script (help.py) to establish an infinite communication loop with the C2 server and receive commands, and a C++-based malware (diagsvc.exe aka DownEx) that is used for data exfiltration.
“During our investigation, we have identified multiple samples of new malware written in C++. The executable diagsvc.exe was stored in folder C:\ProgramData\Programs and is designed for files exfiltration.” continues the report. “One of the samples included a PDB string “C:\Projects\DOWN\Release\DOWN.pdb”. PDB (Program DataBase) is a file format used by Microsoft Visual Studio for storing debugging information about an executable or DLL file. We decided to call this malware family DownEx by combining the DOWN project name with its intended purpose (Exfiltration).”
The researchers also spotted a VBScript-based version of DownEx malware that is used in a fileless version of the attack, this means that the DownEx script is executed directly in memory.
“This attack highlights the sophistication of a modern cyberattack. Cybercriminals are finding new methods for making their attacks more reliable.” concludes the report.
We are in the final!
Please vote for Security Affairs (https://securityaffairs.com/) as the best European Cybersecurity Blogger Awards 2022 – VOTE FOR YOUR WINNERS
Vote for me in the sections where is reported Securityaffairs or my name Pierluigi Paganini
Please nominate Security Affairs as your favorite blog.
Nominate Pierluigi Paganini and Security Affairs here here: https://docs.google.com/forms/d/e/1FAIpQLSepvnj8b7QzMdLh7vWEDQDqohjBUsHyn3x3xRdYGCetwVy2DA/viewform
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, DownEx malware)
The post DownEx cyberespionage operation targets Central Asia appeared first on Security Affairs.