A DDoS botnet dubbed AndoryuBot has been observed exploiting an RCE, tracked as CVE-2023-25717, in Ruckus access points.
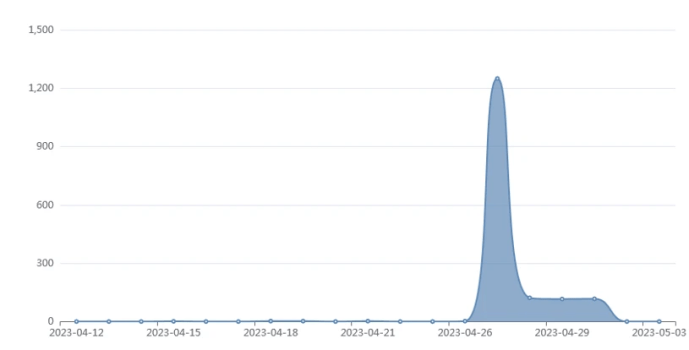
FortiGuard Labs researchers have recently observed a spike in attacks attempting to exploit the Ruckus Wireless Admin remote code execution vulnerability tracked as CVE-2023-25717. The activity is associated with a known DDoS botnet tracked as AndoryuBot that first appeared in February 2023. The bot supports multiple DDoS attack techniques and uses SOCKS5 proxies for C2 communications.
The issue affects Ruckus Wireless Admin version 10.4 and earlier used by multiple Ruckus wireless Access Point (AP) devices. A remote, unauthenticated attacker can exploit the vulnerability to execute arbitrary code and take complete control of a vulnerable device.
Fortinet researchers also reported that a Proof-of-Concept (PoC) code for this vulnerability is publicly available and urges owners to install the patch as soon as possible.
Once compromised a device, the AndoryuBot downloads a script from the URL http[:]//163[.]123[.]142[.]146 for further propagation.
“Once a target device is compromised, AndoryuBot quickly spreads and begins communicating with its C2 server via the SOCKS protocol. In a very short time, it is updated with additional DDoS methods and awaits attack commands.” states the report published by Fortinet. “Users should be aware of this new threat and actively apply patches on affected devices as soon as they become available.”
The variant analyzed by the researchers targets multiple architectures, including arm, m68k, mips, mpsl, sh4, spc, and x86.
Once the communication channel has been set up, the client waits for a command from the C2 server to launch a DDoS attack. AndoryuBot supports 12 DDoS attack methods: tcp-raw, tcp-socket, tcp-cnc, tcp-handshake, udp-plain, udp-game, udp-ovh, udp-raw, udp-vse, udp-dstat, udp-bypass, and icmp-echo.
Once the bot receives the attack command, it starts a DDoS attack on a specific IP address and port number.
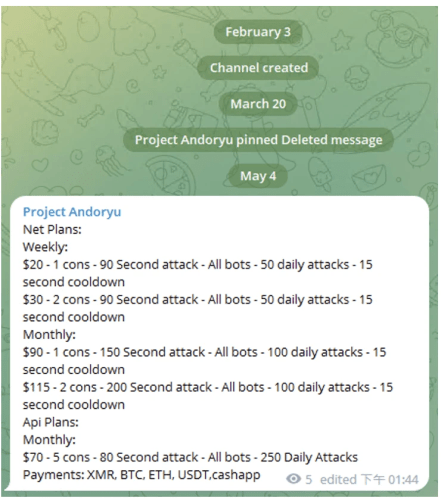
The botnet is advertised on a Telegram channel, below are the prices for DDoS attacks:
Fortinet published indicators of compromise (IoCs) for recent attacks associated with the botnet.
We are in the final!
Please vote for Security Affairs (https://securityaffairs.com/) as the best European Cybersecurity Blogger Awards 2022 – VOTE FOR YOUR WINNERS
Vote for me in the sections where is reported Securityaffairs or my name Pierluigi Paganini
Please nominate Security Affairs as your favorite blog.
Nominate Pierluigi Paganini and Security Affairs here here: https://docs.google.com/forms/d/e/1FAIpQLSepvnj8b7QzMdLh7vWEDQDqohjBUsHyn3x3xRdYGCetwVy2DA/viewform
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, DDoS)
The post Fortinet warns of a spike of the activity linked to AndoryuBot DDoS botnet appeared first on Security Affairs.