A new malware, dubbed Domino, developed by the FIN7 cybercrime group has been used by the now-defunct Conti ransomware gang.
IBM Security X-Force researchers recently discovered a new malware family, called Domino, which was created by developers associated with the FIN7 cybercriminal group (tracked by X-Force as ITG14).
FIN7 is a Russian criminal group (aka Carbanak) that has been active since mid-2015, it focuses on restaurants, gambling, and hospitality industries in the US to harvest financial information that was used in attacks or sold in cybercrime marketplaces.
IBM Security X-Force reported that former members of the now-defunct Conti gang have been using Domino since at least late February 2023. The threat actors used the malware to deliver either the Project Nemesis information stealer or other backdoors and tools such as Cobalt Strike.
This discovery is very important because demonstrates the cooperation among the groups and their members.
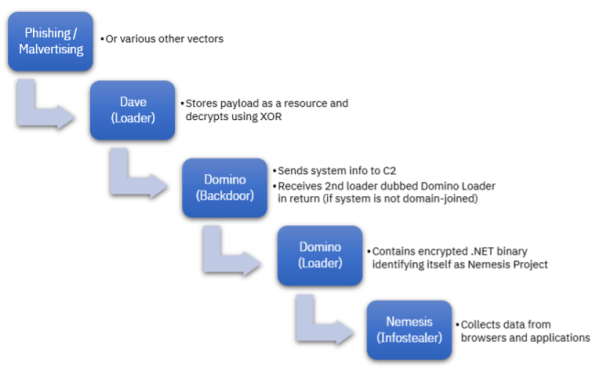
“Since late February 2023, Domino Backdoor campaigns have been observed using the Dave Loader, which we have linked to the Trickbot/Conti syndicate and its former members.” reads the report published by IBM Security X-Force. “Domino’s code shows overlap with the Lizar (aka Tirion, Diceloader) malware family, leading us to suspect that it was created by current or former ITG14 developers. One of Domino’s final payloads is the Project Nemesis infostealer. Project Nemesis was first advertised on the dark web in December 2021, though has been rarely used since then.”
In attacks on higher-value targets instead of downloading the Project Nemesis, the Domino Backdoor contacts a C2 to download post-exploitation tools such as Cobalt Strike.
The researchers noticed that Domino Backdoor and Loader share code overlap with the Lizar Malware (aka Tirion and DiceLoader), which is part of the FIN7’s arsenal. Domino and DiceLoader also share the same configuration structure and have similar bot ID formats.
Lizar was used by FIN7 between March 2020 and the end of 2022, while Domino has been used since at least October 2022, when the use of the Lizar malware began to decrease.
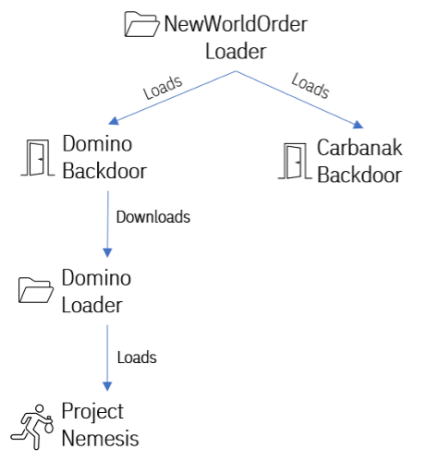
The experts identified Domino Backdoor samples from December 2022, which used a different loader tracked as NewWorldOrder Loader (ThunderboltService.exe), used to load the Project Nemesis Stealer.
In the same period, IBM researchers uncovered NewWorldOrder Loader samples, with the same filename ThunderboltService.exe, used to load the FIN7’s Carbanak Backdoor.
“Domino has been used to install Project Nemesis since at least October 2022 — prior to its use in late February 2023 by ex-Conti actors. This leads us to assess that the ITG14 members responsible for developing Domino probably had a relationship with Project Nemesis and offered Domino and the infostealer to the ex-Conti threat actors as a package.” continues the report. “The ex-Conti members in turn likely used the Project Nemesis infostealer against lower value targets.”
Both the Domino backdoor and the loader are 64-bit DLLs written in Visual C++ and have been used to deliver Project Nemesis since at least October 2022.
“This analysis highlights the intricate relationships between cybercriminal groups and their members.” concludes the report. “The use of malware with ties to multiple groups in a single campaign — such as Dave Loader, Domino Backdoor and Project Nemesis Infostealer — highlights the complexity involved in tracking threat actors but also provides insight into how and with whom they operate.”
Please vote for Security Affairs (https://securityaffairs.com/) as the best European Cybersecurity Blogger Awards 2022 – VOTE FOR YOUR WINNERS
Vote for me in the sections:
- The Teacher – Most Educational Blog
- The Entertainer – Most Entertaining Blog
- The Tech Whizz – Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: https://docs.google.com/forms/d/e/1FAIpQLSfaFMkrMlrLhOBsRPKdv56Y4HgC88Bcji4V7OCxCm_OmyPoLw/viewform
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, FIN7)
The post The intricate relationships between the FIN7 group and members of the Conti ransomware gang appeared first on Security Affairs.