Poland intelligence linked the Russian APT29 group to a series of attacks targeting NATO and European Union countries.
Poland’s Military Counterintelligence Service and its Computer Emergency Response Team linked a recent string of attacks targeting NATO and European Union countries to the Russia-linked APT29 group (aka SVR group, Cozy Bear, Nobelium, and The Dukes).
APT29 along with APT28 cyber espionage group was involved in the Democratic National Committee hack and the wave of attacks aimed at the 2016 US Presidential Elections.
In early March, BlackBerry researchers uncovered a new cyber espionage campaign aimed at EU countries. The hackers targeted diplomatic entities and systems transmitting sensitive information about the region’s politics, aiding Ukrainian citizens fleeing the country, and providing help to the government of Ukraine.
The Polish intelligence states that many elements of the recent campaign, including the infrastructure, the techniques used and the tools, overlap with past APT29 activity.
The recent attacks, which are still ongoing, differ from the previous ones in the use of unique and previously undocumented tools.
The Military Counterintelligence Service and CERT.PL recommend organizations in the area of interest of the APT group to improve the security of IT Security systems.
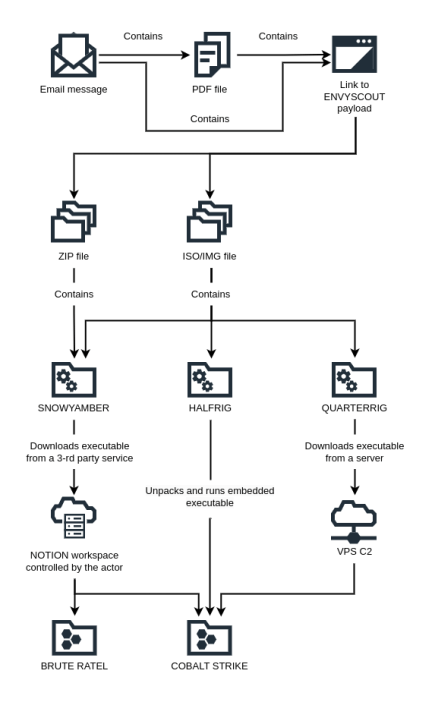
The attack chain commences with a spear-phishing email containing a weaponized document, which contains a link leading to the download of an HTML file. The HTLM files are hosted on a legitimate online library website that was likely compromised by the threat actors sometime between the end of January 2023 and the beginning of February 2023.
“One of the lures appeals to those who want to find out the Poland Ambassador’s schedule for 2023. It overlaps with Ambassador Marek Magierowski’s recent visit to the United Statesp; specifically, his talk on February 2, where he discussed the war in Ukraine at the Catholic University of America Columbus School of Law, also known as the Catholic Law, which is based in Washington, DC.” reads the analysis published by BlackBerry.
The APT29 group also abused multiple legitimate systems, including LegisWrite and eTrustEx, which are used by EU nations for exchanging info and data in a secure way.

“The actor used various techniques to get the user to launch the malware. One of them was a Windows shortcut (LNK) file pretending to be a document but actually running a hidden DLL library with the actor’s tools.” reads the report published by the Poland government. “The DLL Sideloading technique was also observed, using a signed executable file to load and execute code contained in a hidden DLL library by placing it in the same directory, under a name chosen according to the entries in the import table. At a later stage of the campaign, the name of the executable file contained many spaces to make the exe extension difficult to spot.”
The threat actors used the EnvyScout dropper to drop downloaders such as SNOWYAMBER and QUARTERRIG, which in turn deliver additional payloads, including the HALFRIG tool.
“The SNOWYAMBER and QUARTERRIG tools were used as so-called downloaders. Both tools sent the IP address as well as the computer and user name to the actor. They were used to assess whether the victim was of interest to the actor and whether it was a malware analysis environment.” continues the report. “If the infected workstation passed manual verification, the aforementioned downloaders were used to deliver and start-up the commercial tools COBALT STRIKE or BRUTE RATEL. HALFRIG, on the other hand, works as a so-called loader – it contains the COBALT STRIKE payload and runs it automatically.”
The Polish authorities also provided indicators of compromise (IoCs) related to this campaign.
Please vote for Security Affairs (https://securityaffairs.com/) as the best European Cybersecurity Blogger Awards 2022 – VOTE FOR YOUR WINNERS
Vote for me in the sections:
- The Teacher – Most Educational Blog
- The Entertainer – Most Entertaining Blog
- The Tech Whizz – Best Technical Blog
- Best Social Media Account to Follow (@securityaffairs)
Please nominate Security Affairs as your favorite blog.
Nominate here: https://docs.google.com/forms/d/e/1FAIpQLSfaFMkrMlrLhOBsRPKdv56Y4HgC88Bcji4V7OCxCm_OmyPoLw/viewform
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, NATO)
The post The Russia-linked APT29 is behind recent attacks targeting NATO and EU appeared first on Security Affairs.