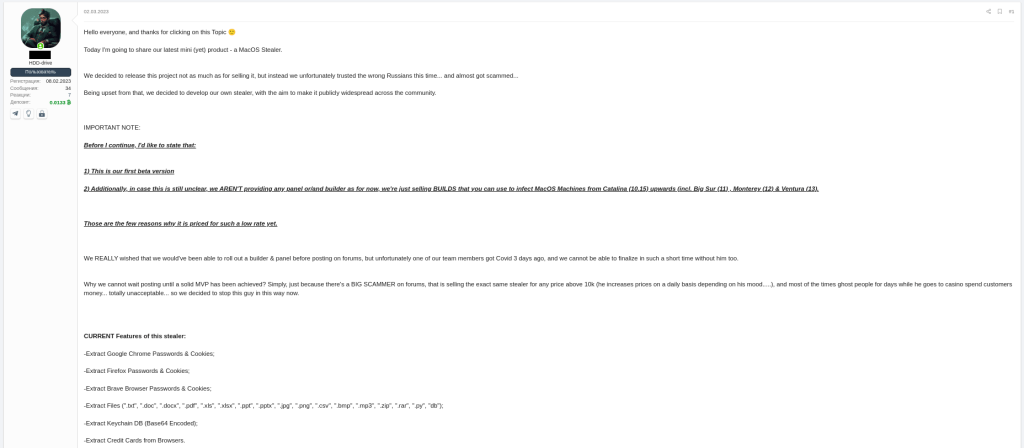
A new MacStealer macOS malware allows operators to steal iCloud Keychain data and passwords from infected systems.
Uptycs researchers team discovered a new macOS information stealer, called MacStealer, which allows operators to steal iCloud Keychain data and passwords from infected systems.
The macOS malware can steal documents, credit card data, cookies from a victim’s browser (i.e. Firefox, Google Chrome, and Brave browsers), and login information.
The malicious code can steal Microsoft Office files, images, archives, and Python scripts.
It can infect Catalina and subsequent macOS versions running on Intel M1 and M2 CPUs.
The operators can control its MacStealers’ operations over Telegram.
The malware was advertised on cybercrime forums since early March, it is under active development and its operators planned to add new features to capture data from Apple’s Safari browser and the Notes app.
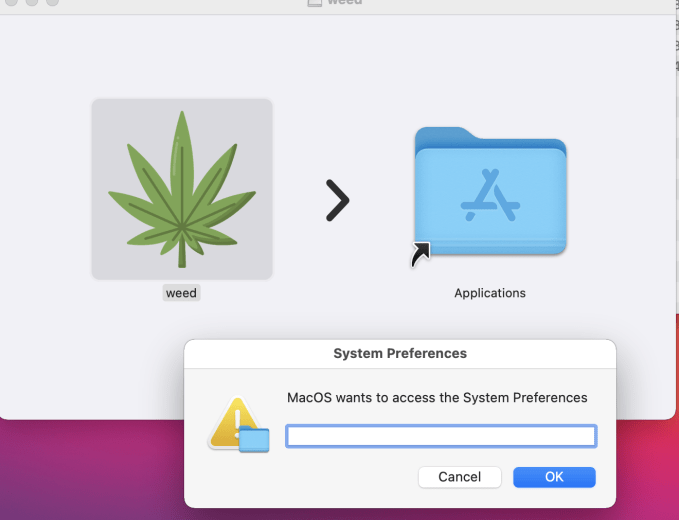
The malware spreads through a .DMG file, and upon opening the file, it opens a fake password prompt to gather passwords using a command line.
“Once the user enters their login credentials, the stealer gathers data as described in the MacStealer’s features section. It stores it in the following system directory.
“/var/folders/{name}/{randomname}/T/{randomname}/files/{different folders}”
The stealer then ZIPs up the data and sends it to C2 via a POST request using a Python User-Agent request (figures 8 and 9).” reads the analysis published by Uptycs. “It deletes the data and ZIP file from the victim’s system during a subsequent mop-up operation.”
The MacStealer transmits selected information to the listed Telegram channels.
The report also provides Indicators of Compromise (IoCs).
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, MacStealer macOS malware)
The post New MacStealer macOS malware appears in the cybercrime underground appeared first on Security Affairs.