Researchers released a PoC exploit code for a high-severity vulnerability in Veeam Backup & Replication (VBR) software.
Veeam recently addressed a high-severity flaw, tracked as CVE-2023-27532, in Veeam Backup and Replication (VBR) software. An unauthenticated user with access to the Veeam backup service (TCP 9401 by default) can exploit the flaw to request cleartext credentials.
A remote attacker can exploit the flaw to access the backup systems of a target organization and execute arbitrary code as ‘SYSTEM.’
“Vulnerability CVE-2023-27532 in a Veeam Backup & Replication component allows an unauthenticated user operating within the backup infrastructure network perimeter to obtain encrypted credentials stored in the configuration database.” reads the advisory published by the vendor. “This may lead to an attacker gaining access to the backup infrastructure hosts.”
The company addressed the flaw with the release of Veeam Backup & Replication build numbers:
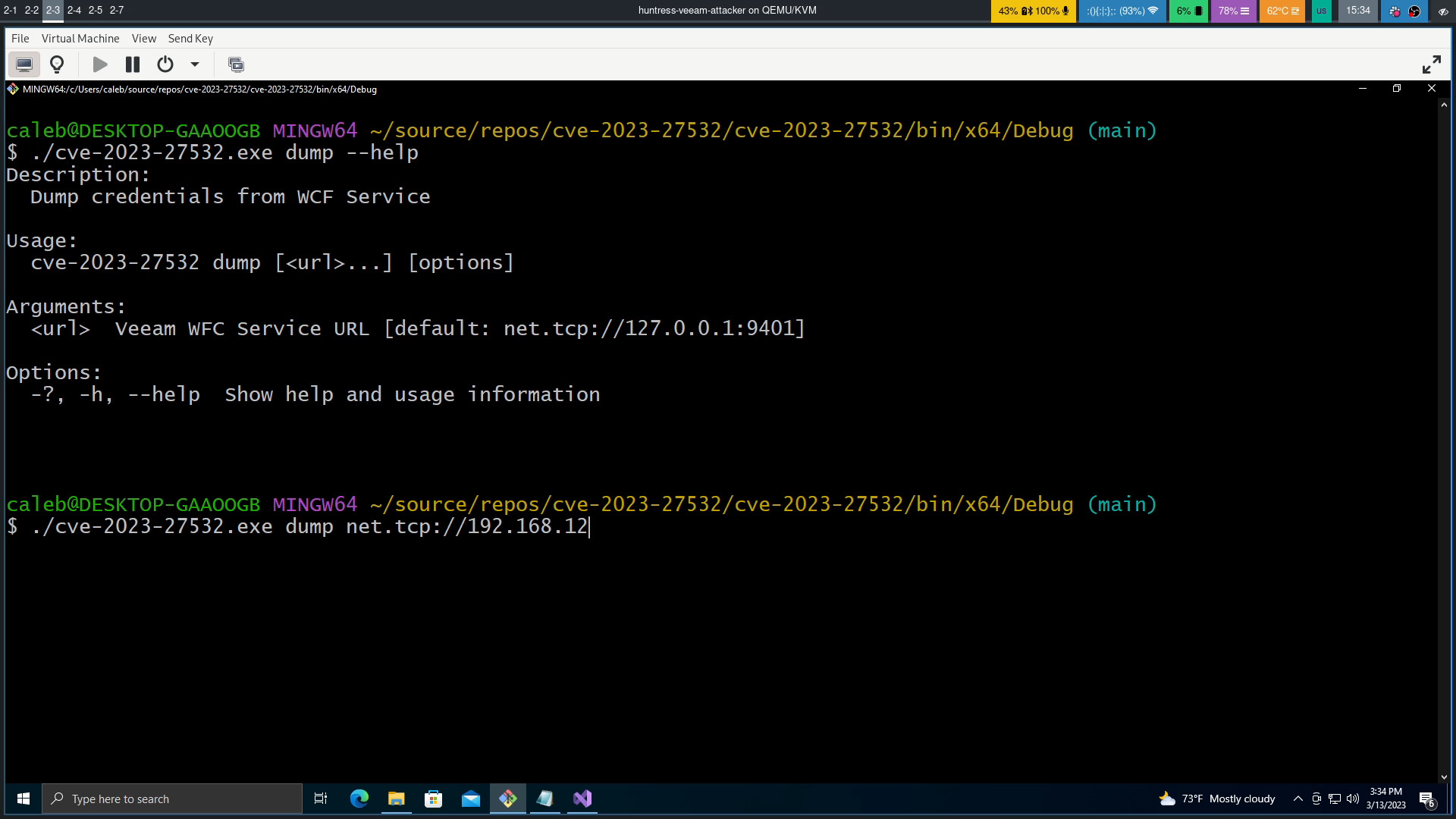
The researchers at Horizon3’s Attack Team published technical details for this vulnerability along with a PoC exploit code.
The researchers performed reverse engineering of Veeam’s Backup Service, they focused on the port used by the Veeam backup service.
The researchers discovered that is possible to abuse an unsecured API endpoint to retrieve credentials in plaintext from the VBR configuration database.
?“We have examined the vulnerable port, reverse engineered the Veeam Backup Service, and constructed a WCF client using .NET core. We have also shown how to extract credentials from the Veeam database by invoking the CredentialsDbScopeGetAllCreds and CredentialsDbScopeFindCredentials endpoints. Finally, we have released our POC on Github, which is built on .NET core and capable of running on Linux, making it accessible to a wider audience.” reads the analysis published by the experts. “It is important to note that this vulnerability should be taken seriously and patches should be applied as soon as possible to ensure the security of your organization.”
The researchers explained that their work is based on the “great prior research” conducted by researchers from HuntressLabs, @CODE WHITE GmbH, and Y4er_ChaBug.
Veeam Backup & Replication CVE-2023-27532 Response (By HuntressLabs)
Huntress researchers reported that on their install base composed of 2 million devices, they uncovered 7,500 hosts with a vulnerable version of the Veeam Backup & Replication service present.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Backup & Replication)
The post Experts published PoC exploit code for Veeam Backup & Replication bug appeared first on Security Affairs.

