An alleged Chinese threat actor group is behind attacks on government organizations exploiting a Fortinet zero-day flaw (CVE-2022-41328).
A suspected China-linked group is exploiting a Fortinet zero-day vulnerability, tracked as CVE-2022-41328, in attacks aimed at government organizations.
A few days ago, Fortinet researchers warned of an advanced threat actor that is targeting governmental or government-related entities.
The unknown threat actor is exploiting a vulnerability in Fortinet FortiOS software, tracked as CVE-2022-41328, that may allow a privileged attacker to read and write arbitrary files via crafted CLI commands.
The CVE-2022-41328 vulnerability (CVSS score: 6.5) is a path traversal issue in FortiOS can can result in arbitrary code execution.
“A improper limitation of a pathname to a restricted directory vulnerability (‘path traversal’) [CWE-22] in FortiOS may allow a privileged attacker to read and write arbitrary files via crafted CLI commands.” reads the advisory published by Fortinet.
The vulnerability impacts FortiOS versions 6.0, 6.2, 6.4.0 through 6.4.11, 7.0.0 through 7.0.9, and 7.2.0 through 7.2.3. The company addressed the vulnerability with the release of versions 6.4.12, 7.0.10, and 7.2.4 respectively.
Fortinet launched an investigation into the attacks after the FortiGate devices of one customer suddenly halted and failed to reboot. The devices halted displaying the following error message:
“System enters error-mode due to FIPS error: Firmware Integrity self-test failed”
The failure of the integrity test blocks the reboot of the device to protect the integrity of the network.
Mandiant researchers linked a series of attacks that took place in mid-2022 to a China-linked threat actor tracked as UNC3886 by the security firm.
“a suspected China-nexus threat actor likely already had access to victim environments, and then deployed backdoors onto Fortinet and VMware solutions as a means of maintaining persistent access to the environments.” reads the report published by Mandiant. “This involved the use of a local zero-day vulnerability in FortiOS (CVE-2022-41328) and deployment of multiple custom malware families on Fortinet and VMware systems.”
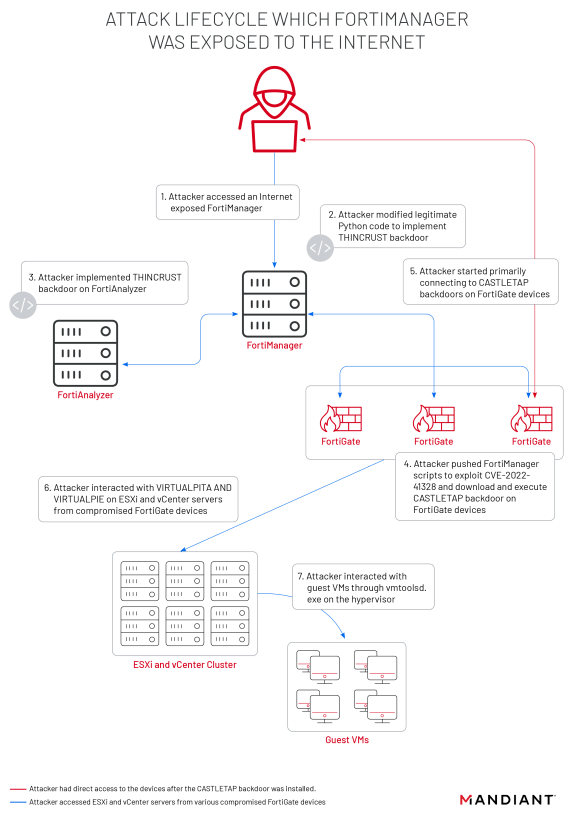
The attackers exploited the CVE-2022-41328 zero-day to write files to FortiGate firewall disks outside of the normal bounds allowed with shell access, then they maintained persistent access with Super Administrator privileges within FortiGate Firewalls through ICMP port knocking.
Threat actors also bypassed the firewall rules active on FortiManager devices with a passive traffic redirection utility. The attackers also used a custom API endpoint created within the device to maintain persistence ùon FortiManager and FortiAnalyzer, then disabled OpenSSL 1.1.0 digital signature verification of system files through targeted corruption of boot files.
Once compromised the Fortinet devices, the threat actors established backdoor access using two previously undocumented malware, a Python-based Thincrust backdoor disguised as legitimate API calls and the ICMP port-knocking Castletap passive backdoor.
Once obtained access to the Fortinet devices, the attackers targeted ESXi servers to deploy malicious vSphere Installation Bundles which contained VIRTUALPITA and VIRTUALPIE backdoors. This allowed the attackers to maintain persistent access to the hypervisors and execute commands on guest virtual machines.
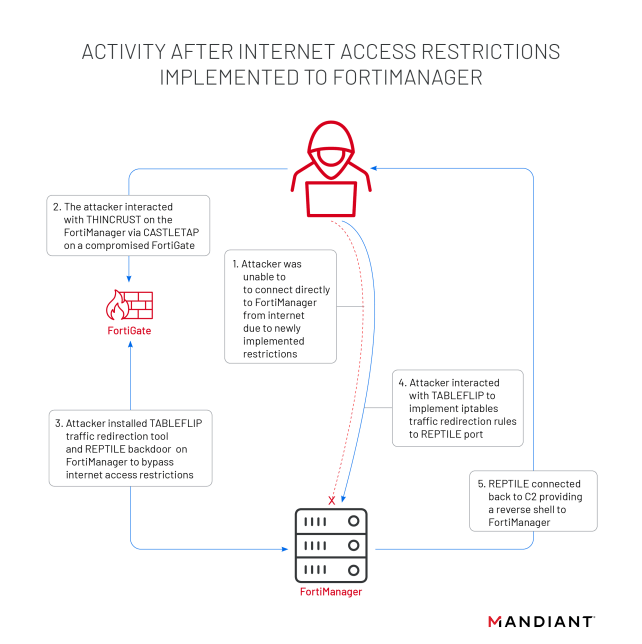
When FortiManager was not exposed to the Internet, the threat actors deployed a traffic redirector (Tableflip) and a passive backdoor (Reptile) to circumvent the new ACLs.
“many network appliances lack solutions to detect runtime modifications made to the underlying operating system and require direct involvement of the manufacturer to collect forensic images. Cross organizational communication and collaboration is key to providing both manufacturers with early notice of new attack methods in the wild before they are made public and investigators with expertise to better shed light on these new attacks.” concludes Mandiant.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Fortinet)
The post China-linked APT likely linked to Fortinet zero-day attacks appeared first on Security Affairs.