The recently discovered Windows ransomware IceFire now also targets Linux enterprise networks in multiple sectors.
SentinelLabs researchers discovered new Linux versions of the recently discovered IceFire ransomware that was employed in attacks against several media and entertainment organizations worldwide. The ransomware initially targeted only Windows-based systems, with a focus on technology companies.
IceFire was first detected in March 2022 by researchers from the MalwareHunterTeam, but the group claimed victims via its dark web leak site since August 2022.
The experts observed threat actors exploiting a deserialization vulnerability in IBM Aspera Faspex file-sharing software (CVE-2022-47986, CVSS score: 9.8) to deploy the ransomware.
Most of IceFire infections were reported in Turkey, Iran, Pakistan, and the United Arab Emirates. Experts pointed out that these contries are typically not a focus for organized ransomware operations.
SentinelOne researchers successfully tested the IceFire Linux version against Intel-based distributions of Ubuntu and Debian. It is 2.18 MB in size, while the 64-bit ELF binary is compiled with gcc for the AMD64 architecture.
In an attack observed by the experts, the ransomware successfully encrypted a CentOS host running a vulnerable version of IBM Aspera Faspex file server software.
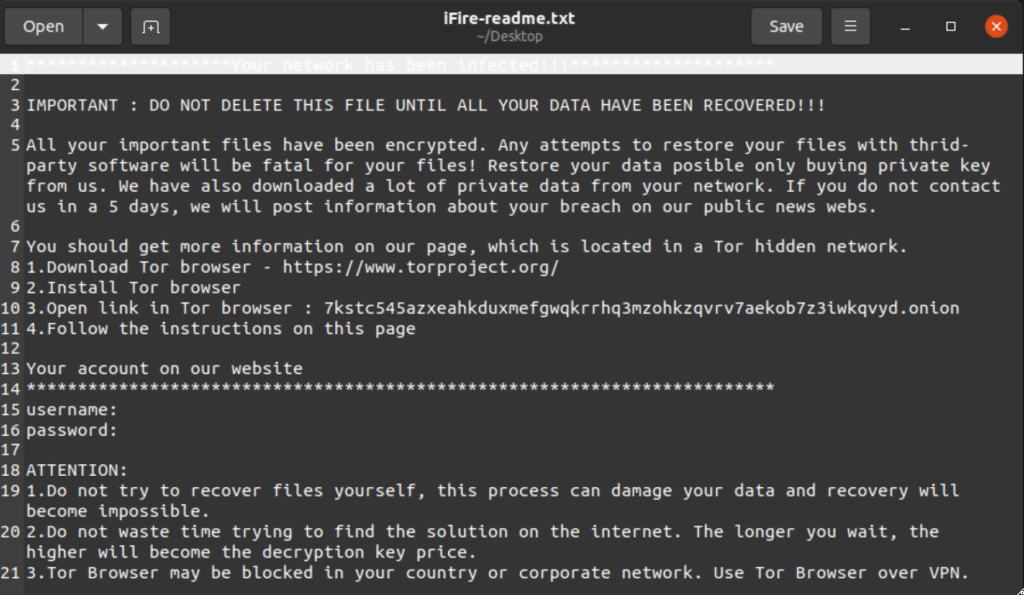
The ransomware encrypts files and appends the “.ifire” extension to the filename, then deletes itself by removing the binary.
IceFire doesn’t encrypt the files with “.sh” and “.cfg” extensions, it also avoids encrypting certain folders so that the infected machine continues to be usable.
“During our analysis, the user profile directory at /home/[user_name]/ saw the most encryption activity. IceFire targets user and shared directories (e.g., /mnt, /media, /share) for encryption; these are unprotected parts of the file system that do not require elevated privileges to write or modify.” reads the analysis published by SentinelOne. “Interestingly, several file sharing clients downloaded benign encrypted files after IceFire had encrypted the file server’s shared folders. Despite the attack on the server, clients were still able to download files from the encrypted server. This implies the IceFire developer made thoughtful choices in the excluded paths and file extensions.”
The Windows version of the ransomware spreads through phishing messages and pivots using post-exploitation toolkits. The Linux variant is still in the early stages.
The experts pointed out that at the time of the publishing of the report, the IceFire binary was detected by 0/61 VirusTotal engines.
The ransom note contains hardcoded credentials to log into the ransom payment portal hosted on a Tor hidden service.
“This evolution for IceFire fortifies that ransomware targeting Linux continues to grow in popularity through 2023. While the groundwork was laid in 2021, the Linux ransomware trend accelerated in 2022 when illustrious groups added Linux encryptors to their arsenal, including the likes of BlackBasta, Hive, Qilin, Vice Society aka HelloKitty, and others.” concludes the experts. “In comparison to Windows, Linux is more difficult to deploy ransomware against–particularly at scale. Many Linux systems are servers: typical infection vectors like phishing or drive-by download are less effective. To overcome this, actors turn to exploiting application vulnerabilities, as the IceFire operator demonstrated by deploying payloads through an IBM Aspera vulnerability.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, IceFire ransomware)
The post Recently discovered IceFire Ransomware now also targets Linux systems appeared first on Security Affairs.

