The TA886 hacking group targets organizations in the United States and Germany with new spyware tracked as Screenshotter.
A recently discovered threat actor, tracked as TA886 by security firm Proofpoint, is targeting organizations in the United States and Germany with new malware dubbed Screenshotter.
The experts first spotted the attacks attributed to this threat actor in October 2022, they believe that the group is financially motivated.
The TA886 group used custom toolset, such as WasabiSeed and Screenshotter, to take screenshots from the victim’s system and evaluate the opportunity to install a bot and stealer.
The attack chain starts with an phishing emails containing a malicious URL or malicious attachment that lead to deployment of WasabiSeed and Screenshotter malware. The researchers also observed the threat actor using conducting post-exploitation activity employing AHK Bot and Rhadamanthys Stealer.
“Since October 2022 and continuing into January 2023, Proofpoint has observed a cluster of evolving financially motivated activity which we are referring to as “Screentime”. The attack chain starts with an email containing a malicious attachment or URL and leads to malware that Proofpoint dubbed WasabiSeed and Screenshotter.” reads the post published by Proofpoint. “Proofpoint is tracking this activity under threat actor designation TA866.”
The threat actor used multiple tools in the delivery stage, including Traffic Distribution System (TDS), malicious, some of which can be purchased from other threat actors in the cybercrime ecosystem.
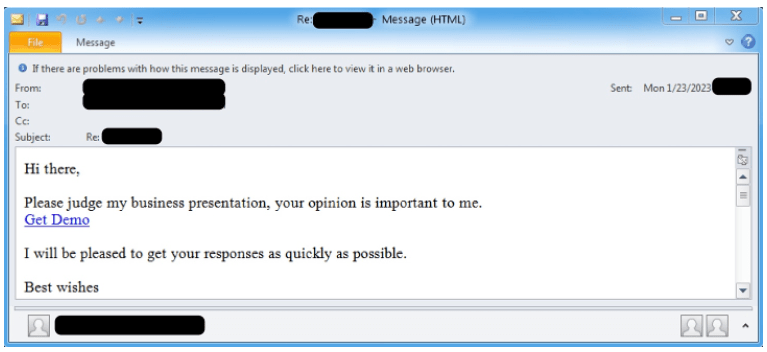
Experts, for example, observed phishing emails using Microsoft Publisher (.pub) attachments with macros, or embedding malicious URLs linking (via 404 TDS) to Publisher files with macros and JavaScript files. In other cases the attackers used PDFs with URLs linking (via 404 TDS) to JavaScript files.
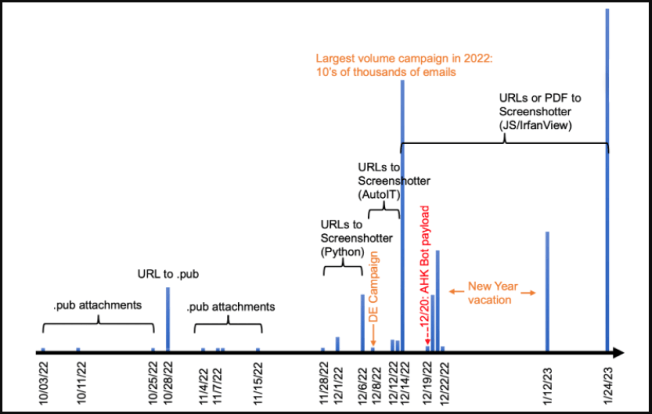
Most of the attacks were observed between October and November 2022 and involved only a limited number of emails (using Publisher files) sent to a small number of companies. Between November and December 2022, the threat actor switched to using URLs and the volume of emails increased drastically.
The campaigns consisted of thousands or even tens of thousands of emails on average, burst of emails were sent two to four times a week. On January 2023, the experts observed a minor number of campaigns, but with greater email volumes.
According to the analysis, upon clicking the URL, the attack chain will start ending with the infection of the recipient’s system with the custom malware Screenshotter.
The malware is able to take JPG screenshots of the victim’s desktop and submitting it to a remote C2 via a POST to a hardcoded IP address.
The gathered images allows threat actor to perform reconnaissance and victim profiling.
The malware also drops additional custom payloads if necessary, including a domain profiler script that sends AD (Active Directory) domain details to the C2 and a loader script (AHK Bot loader) that inject a fileless info stealing malware (dubbed Rhadamanthys) in memory.
Rhadamanthys is an info stealing malware that was initially advertised for sale on underground forums since the middle of 2022. It can steal crypto wallets, steam accounts, passwords from browsers, FTP clients, chat clients (e.g. Telegram, Discord), email clients, VPN configurations, cookies, grab files, and more.
Most of TA886’s activity was observed during a regular workday in the UTC+2 or UCT+3 time zone.
This information, combined with the presence of Russian language variable names and comments in the source code of the AHK Bot loader, suggests that TA886 likely is a Russian threat actor.
“Proofpoint assesses with low to moderate confidence that these campaigns were likely performed by TA866 given the similarities in TTPs but the possibility of the tools being used by more than one actor cannot be completely ruled out. Attribution investigation is ongoing.” concludes the report from Proofpoint.
“The use of Screenshotter to gather information on a compromised host before deploying additional payloads indicates the threat actor is manually reviewing infections to identify high-value targets. The AD profiling is especially concerning as follow-on activities could lead to compromises on all domain-joined hosts.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Screenshotter)
The post New TA886 group targets companies with custom Screenshotter malware appeared first on Security Affairs.