TrickGate is a shellcode-based packer offered as a service to malware authors to avoid detection, CheckPoint researchers reported.
TrickGate is a shellcode-based packer offered as a service, which is used at least since July 2016, to hide malware from defense programs. A packer (aka “Crypter” and “FUD”) implements a series of functionalities to make it harder for antivirus programs to detect the malware.
The Check Point Research team reported that over the last 6 years, TrickGate was used to drop some of the most popular malware families, including Cerber, Trickbot, Maze, Emotet, REvil, Cobalt Strike, AZORult, Formbook, and AgentTesla.
“TrickGate managed to stay under the radar for years because it is transformative – it undergoes changes periodically. This characteristic caused the research community to identify it by numerous attributes and names.” reads the report published by Check Point Research. “While the packer’s wrapper changed over time, the main building blocks within TrickGate shellcode are still in use today.”
The developers of the TrickGate packer continually improve its code, it has been given many names based on its varied attributes. Its names include “TrickGate”, “Emotet’s packer”, “new loader”, “Loncom”, and “NSIS-based crypter.”
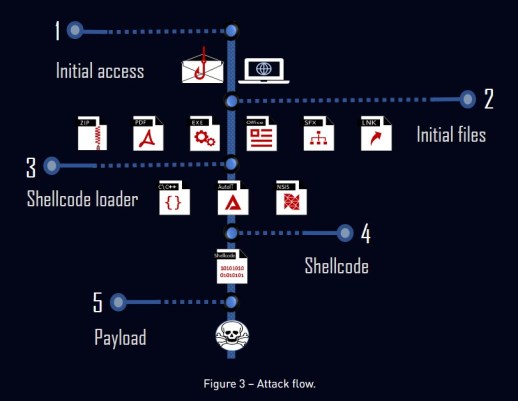
The attack chain observed by the experts can vary significantly, but in most cases, threat actors used phishing messages with malicious attachments or malicious links.
“The first stage mainly comes in the form of an archived executable, but we monitored many file types and delivery permutations that lead to the same shellcode.” continues the report. “The second stage is the shellcode loader which is responsible for decrypting and running the shellcode.”
The second stage is the shellcode loader which is responsible for decrypting and running the shellcode.
The shellcode loader was written in one of the following languages: NSIS script, AutoIT script, and C.
The shellcode is the core of the packer, because it decrypts the payload and stealthily injects it into a new process.
The TrickGate packer was primarily used in attacks aimed at the manufacturing sector, and other attacks aimed at the education, healthcare, government, and finance industries.
The most popular malware families used in the attacks are FormBook (42%), LokiBot (25%), and Agent (11%). Attacks were mainly reported in Taiwan, Turkey, Germany, Russia, and China.
“Understanding the packer’s building blocks is of crucial importance to detect the threat, as blocking the packer will protect against the threat in an early stage, before the payload starts to run.” concludes the report. “Packers often get less attention, as researchers tend to focus their attention on the actual malware, leaving the packer stub untouched. However, the identified packer can now be used as a focal point to detect new or unknown malware.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, packer)
The post TrickGate, a packer used by malware to evade detection since 2016 appeared first on Security Affairs.